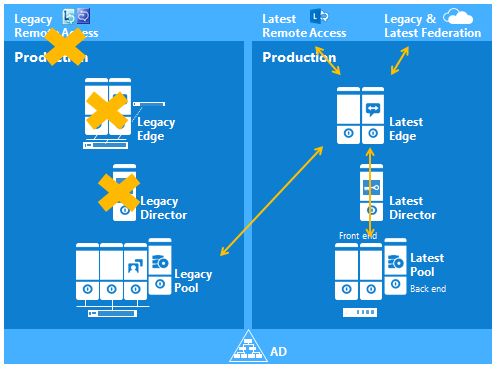
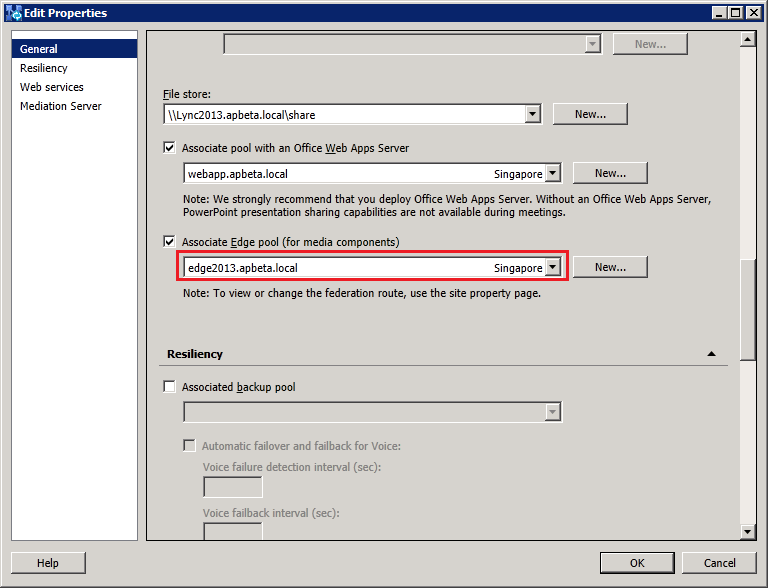
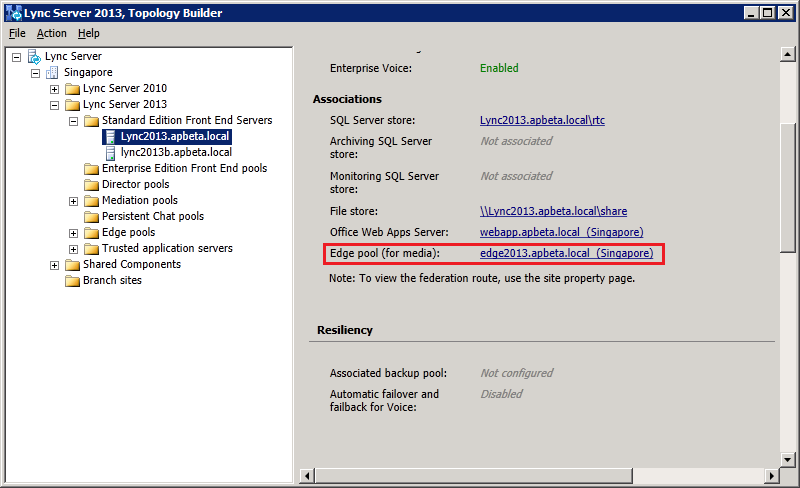
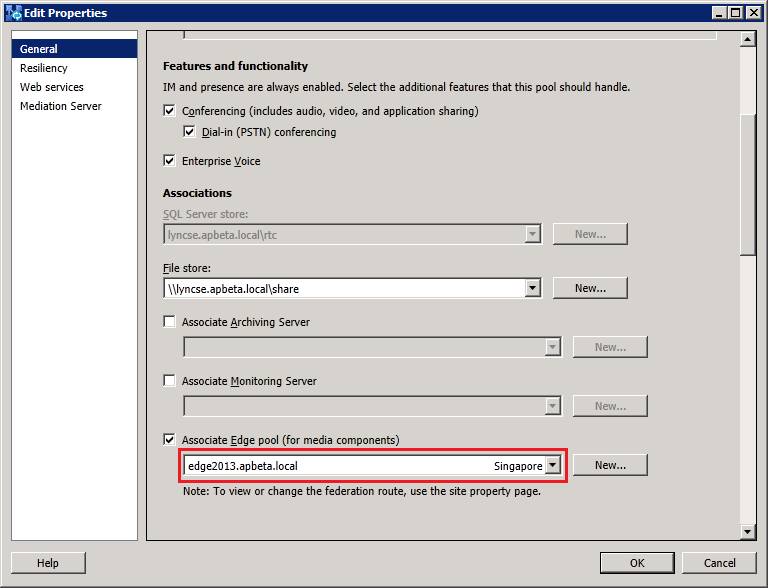
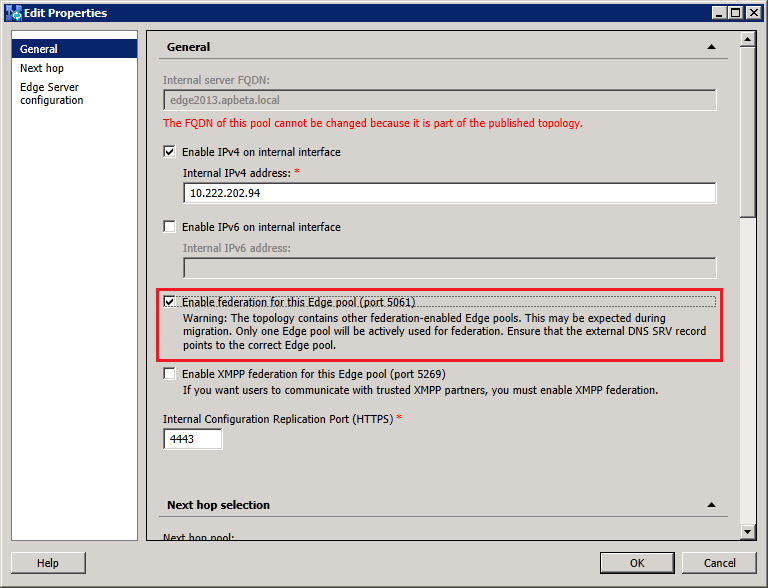
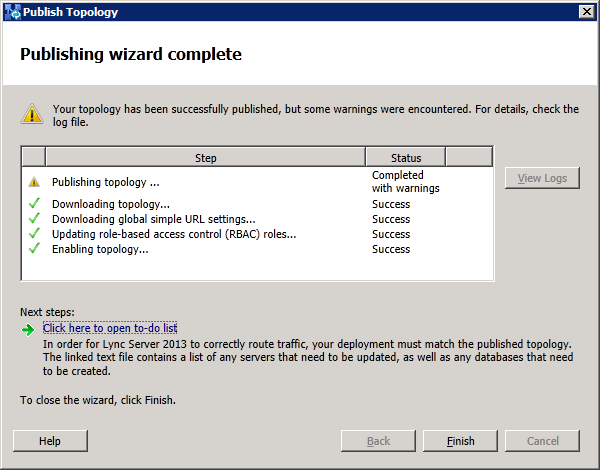
Configure the Lync2013 FE Pool to use the new 2013 Edge
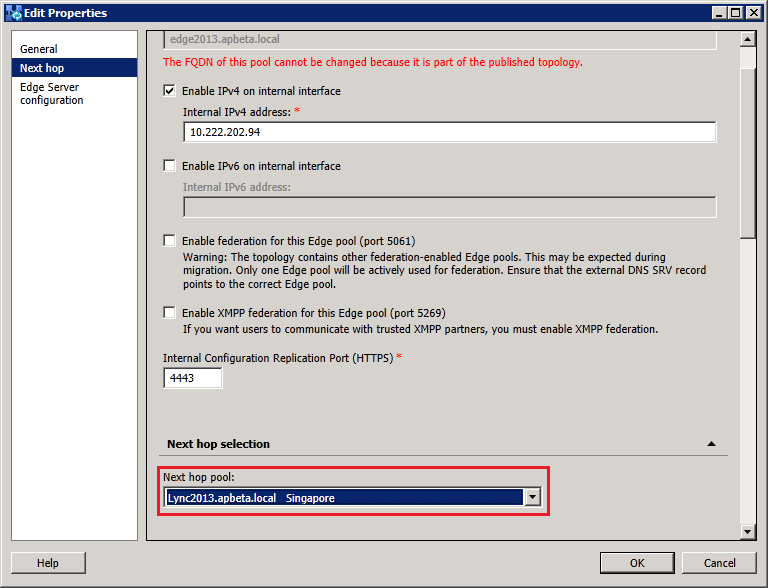
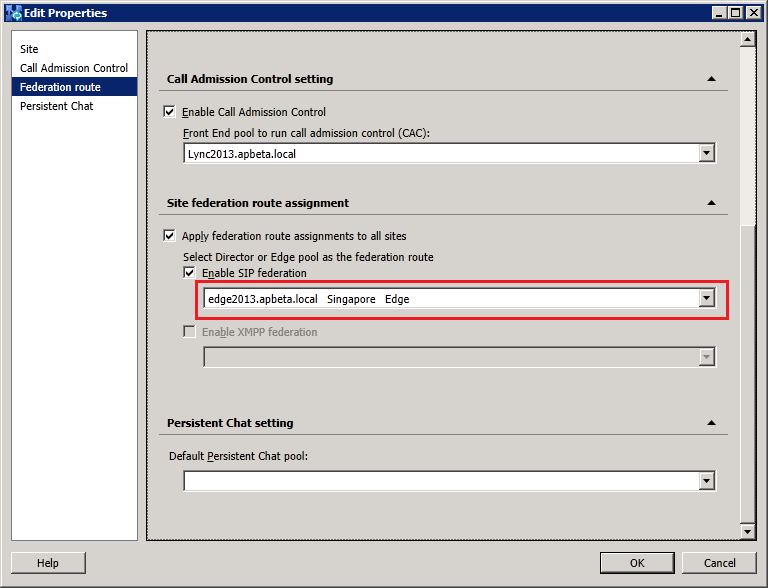
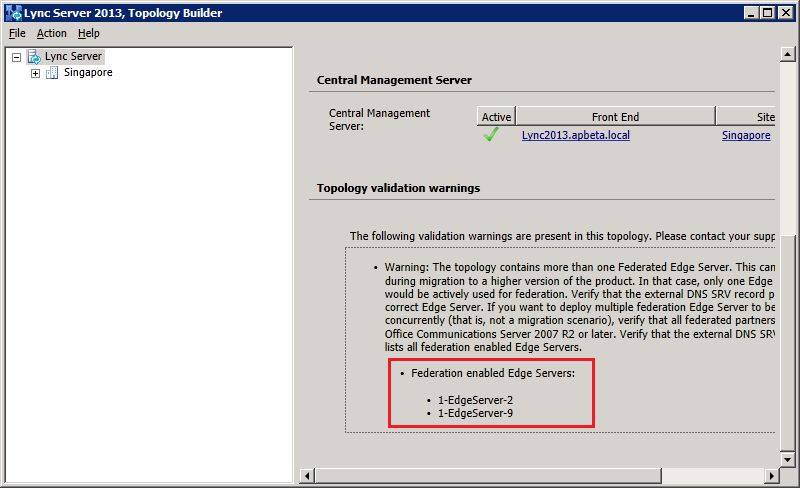
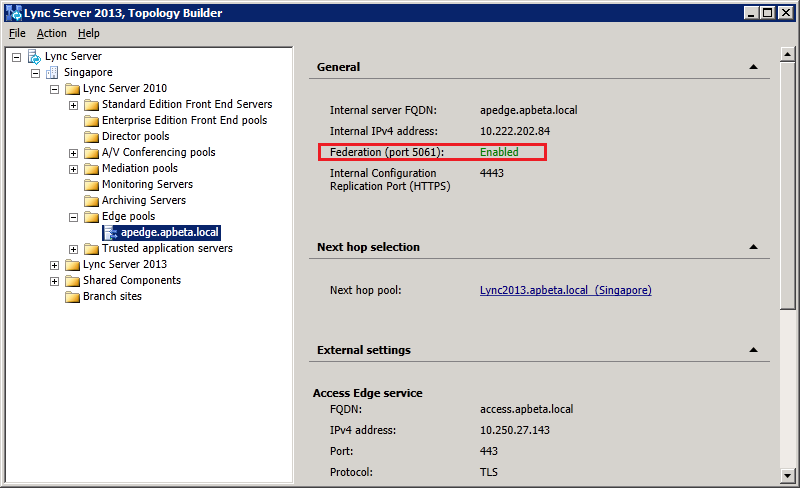
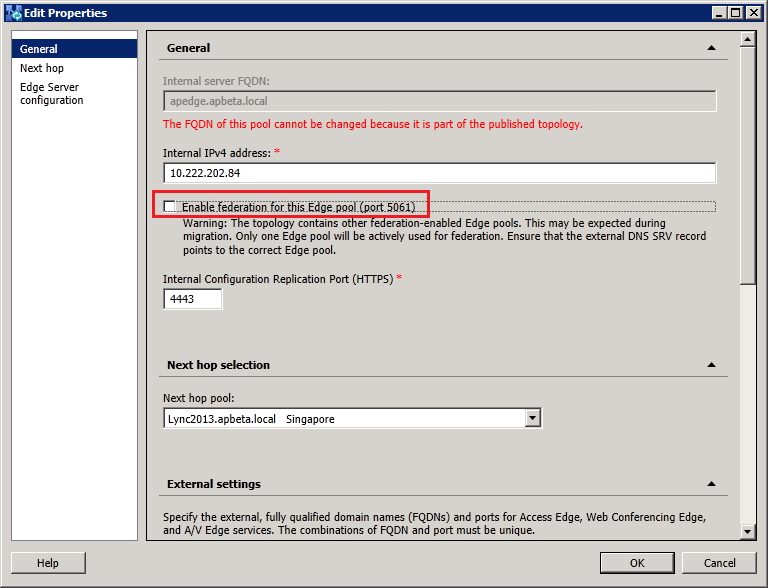
Changing the Federation Route
1. Users from at least one federated domain, an internal user on Lync Server 2013, and a user on Lync Server 2010. Test instant messaging (IM), presence, audio/video (A/V), and desktop sharing.
2. Verify that anonymous users are able to join conferences.
3. A user hosted on Lync Server 2010 using remote user access with a user on Lync Server 2013, and a user on Lync Server 2010. Test IM, presence, A/V, and desktop sharing.
4. A user hosted on Lync Server 2013 using remote user access with a user on Lync Server 2013, and a user on Lync Server 2010. Test IM, presence, A/V, and desktop sharing.


 RSS Feed
RSS Feed