
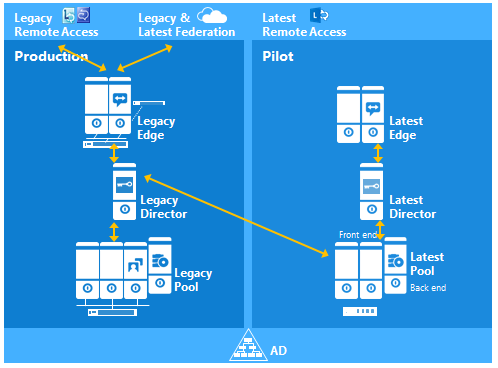
A separate article will be posted later to discuss how to completely migrate all users to the Lync2013 Pool and decommission the legacy Lync2010 components.
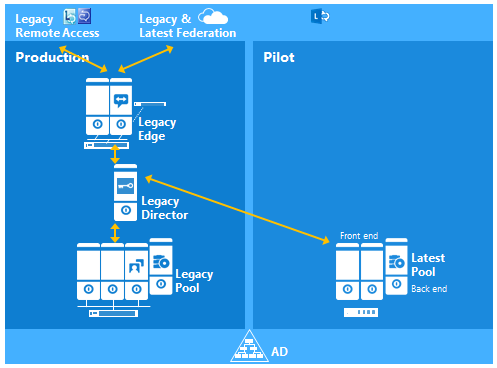
Part I: Connecting the Lync2013 FE Server to the legacy Lync2010 Edge Pool
Part II: Deploying Lync2013 Edge
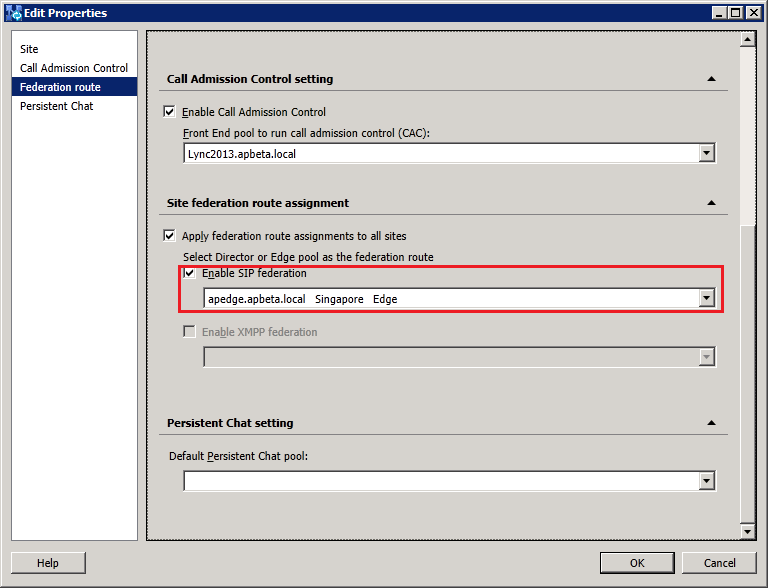
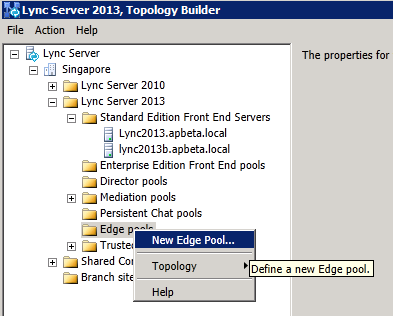
Step 1: Define the new Edge pool in Topology Builder
Step 2: Install Prerequisite software for Lync2013 Edge
Step 3: Deploy the Edge server components
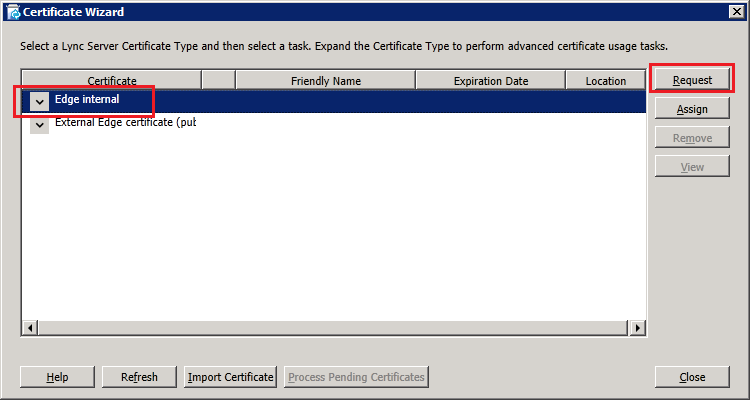
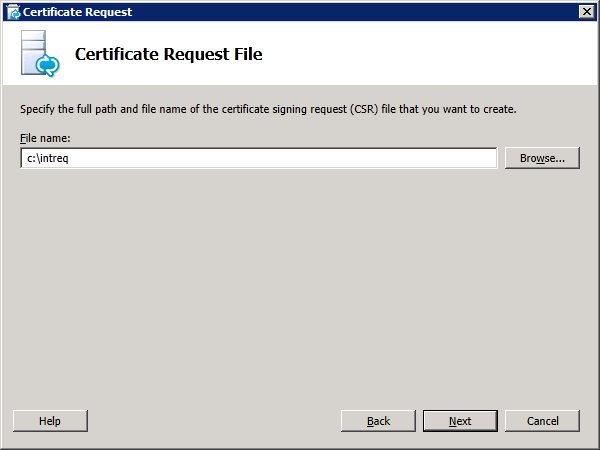
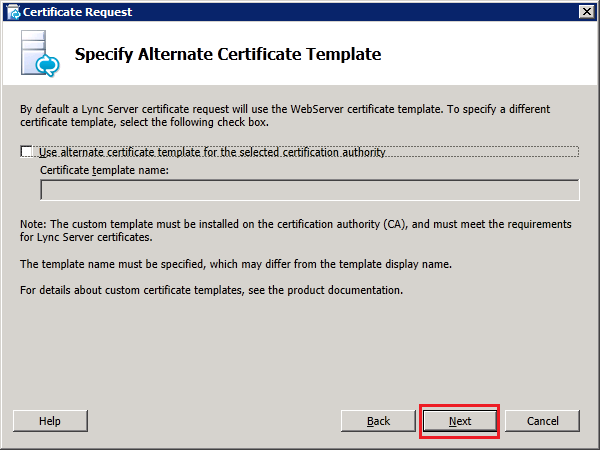
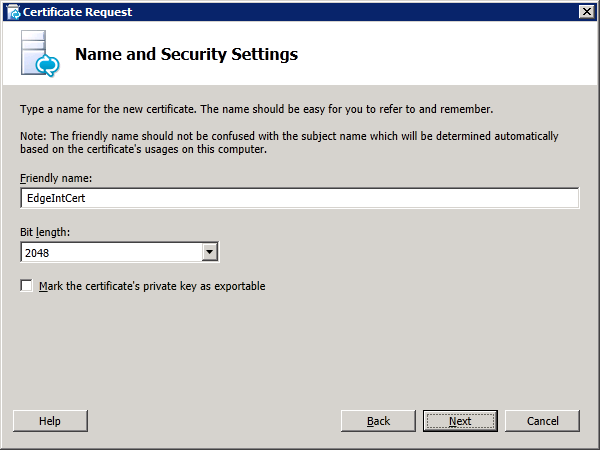
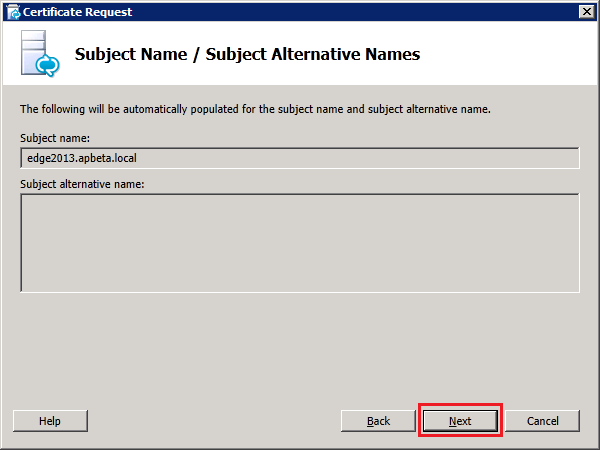
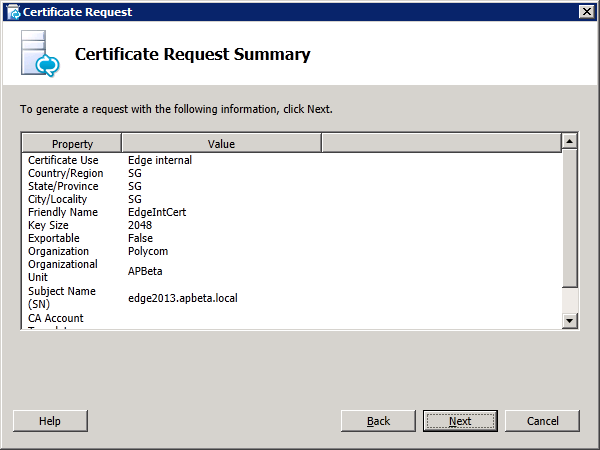
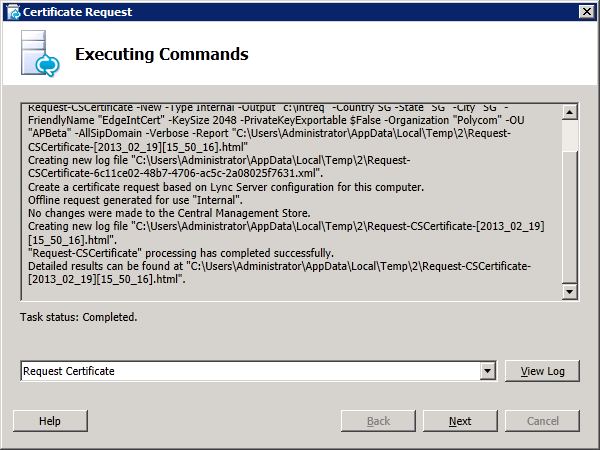
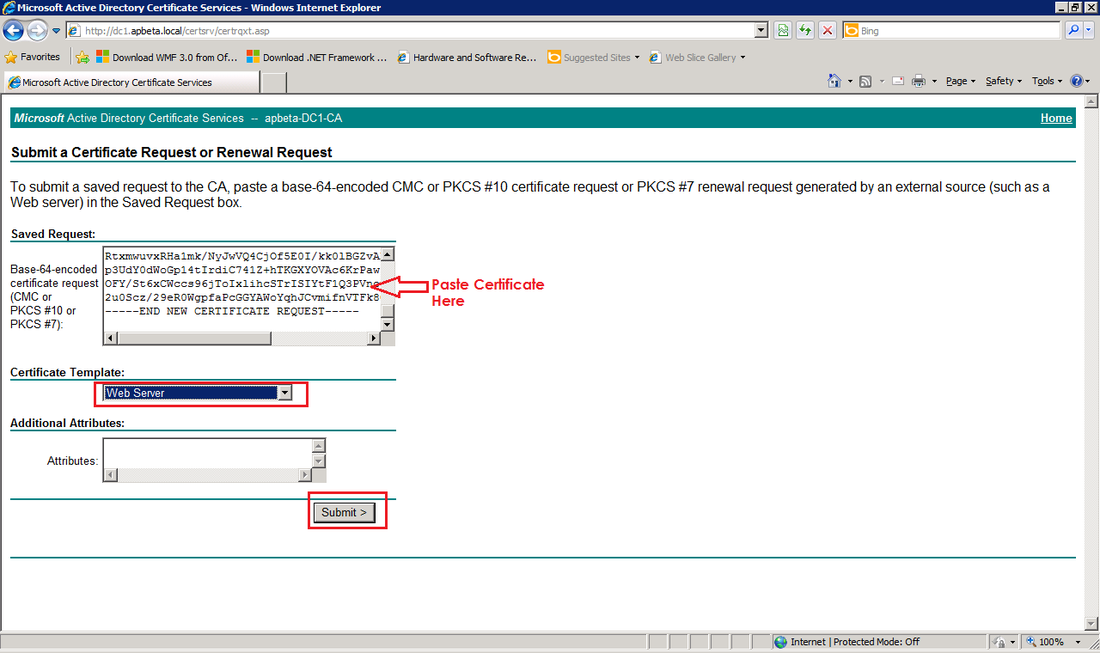
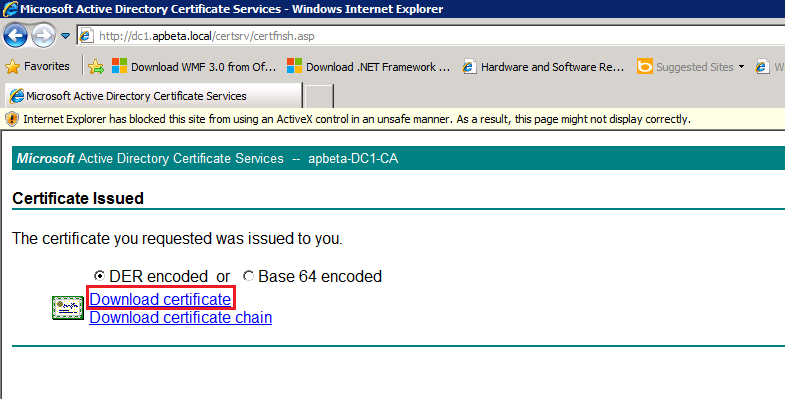
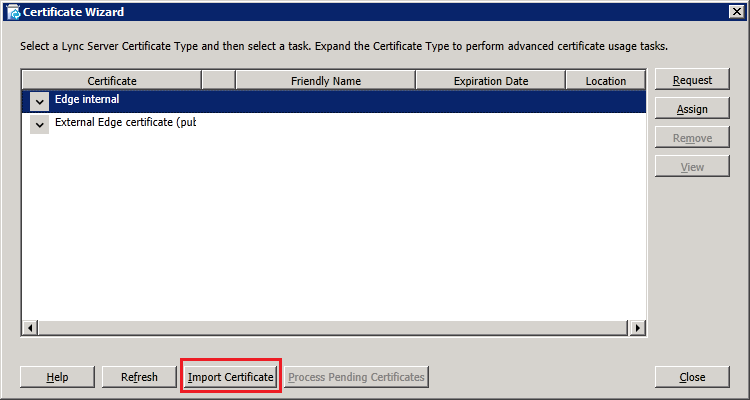
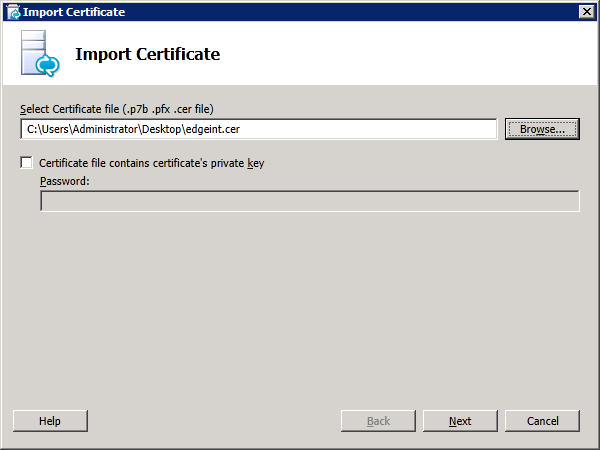
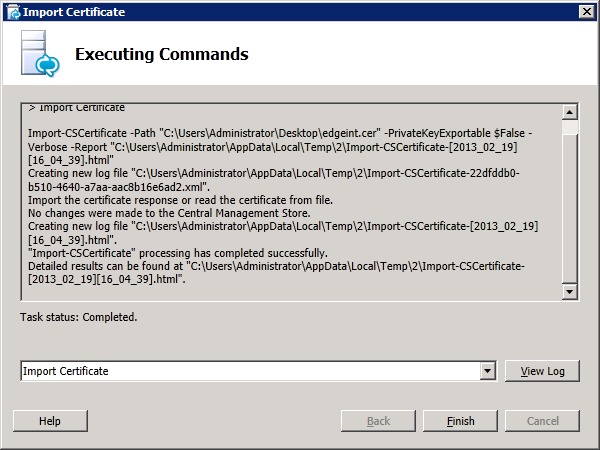
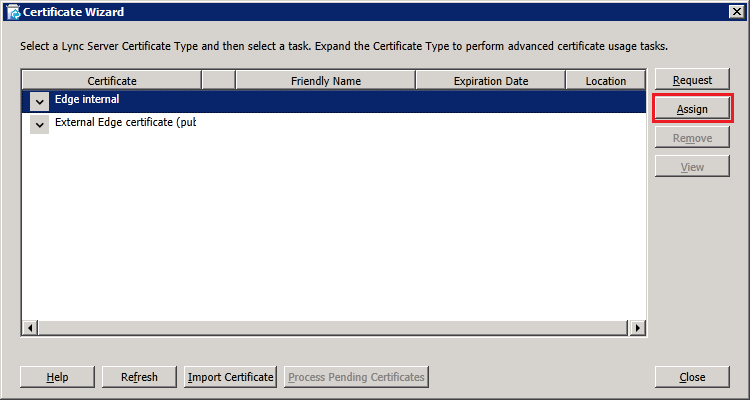
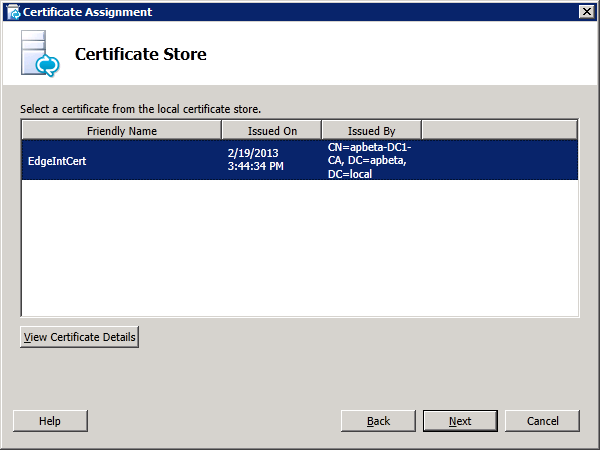
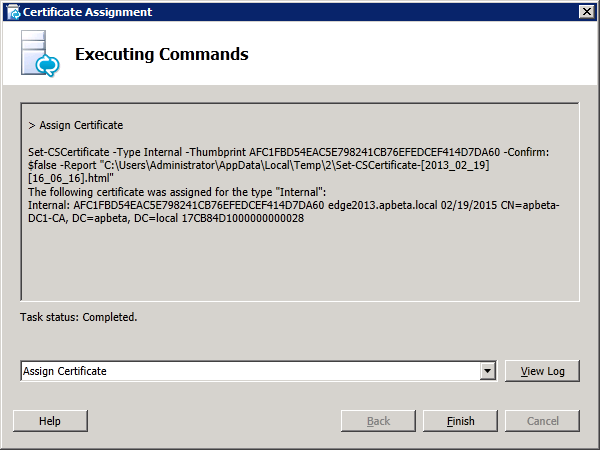
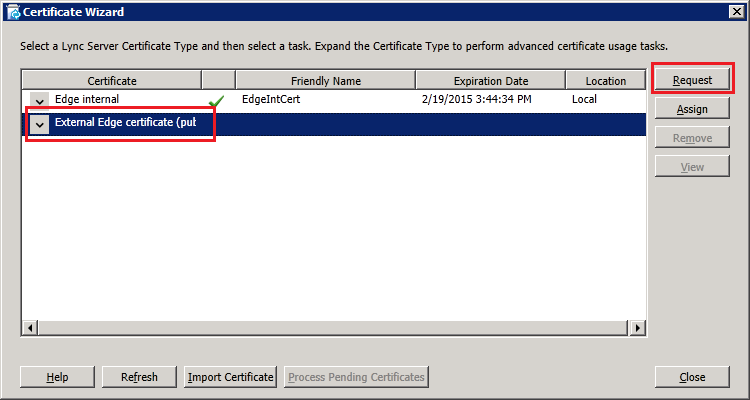
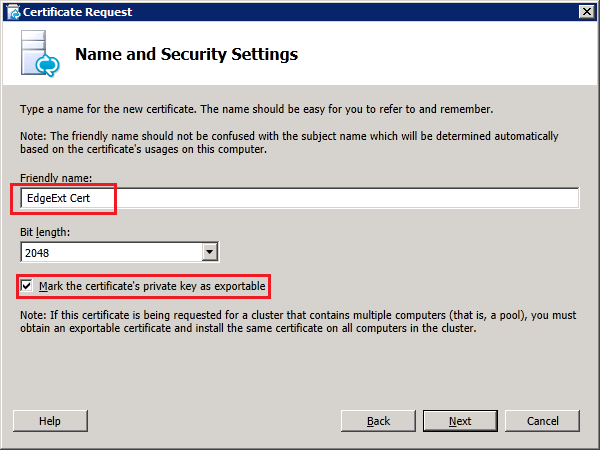
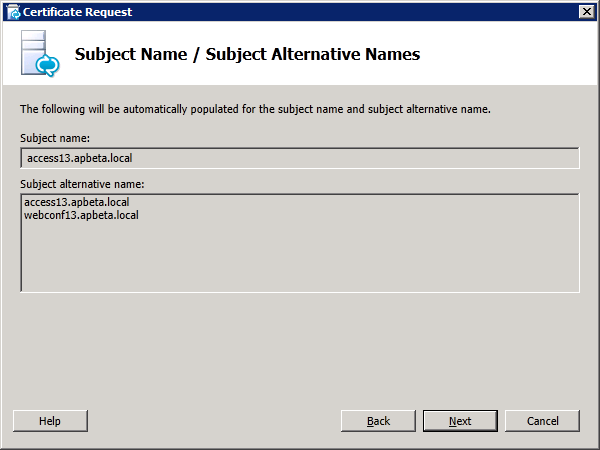
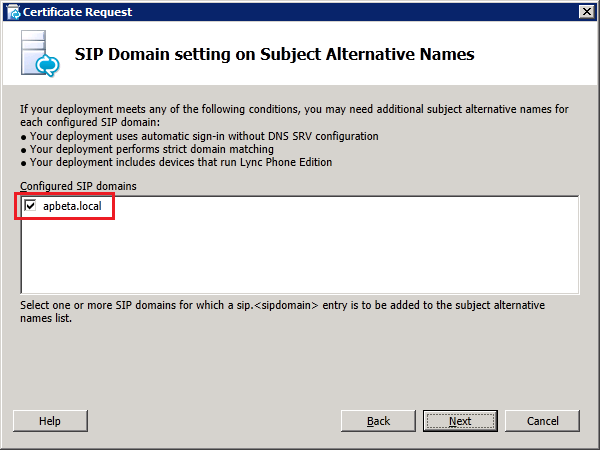
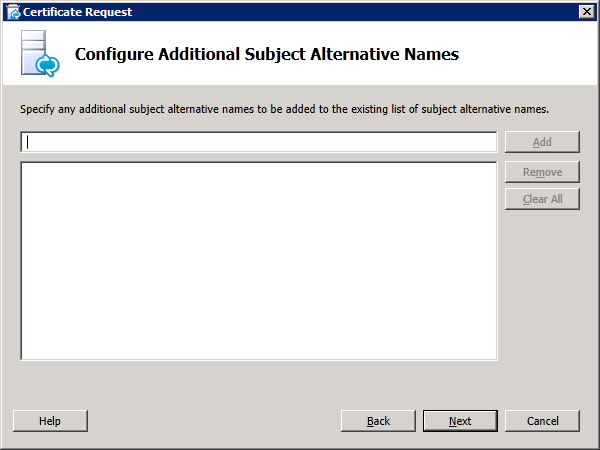
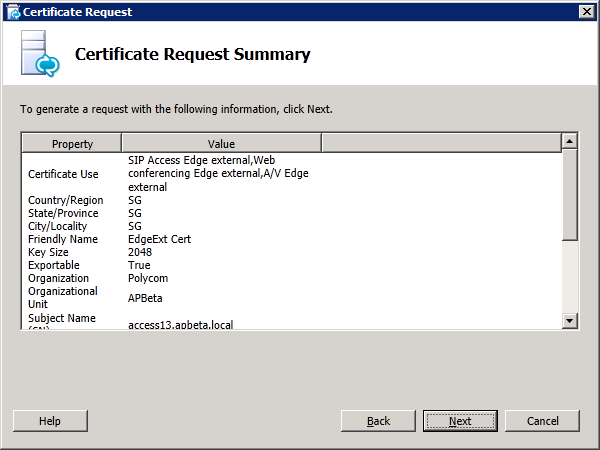
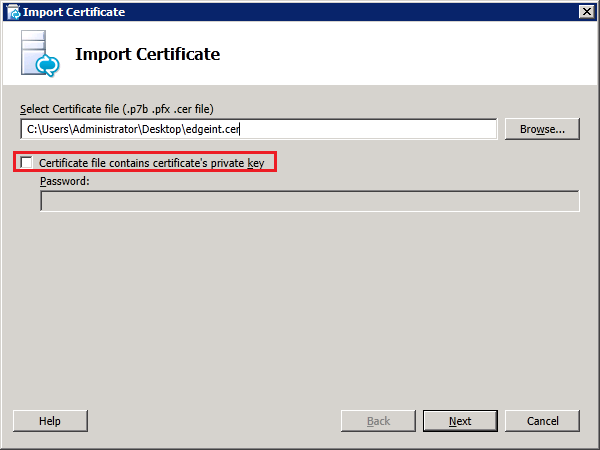
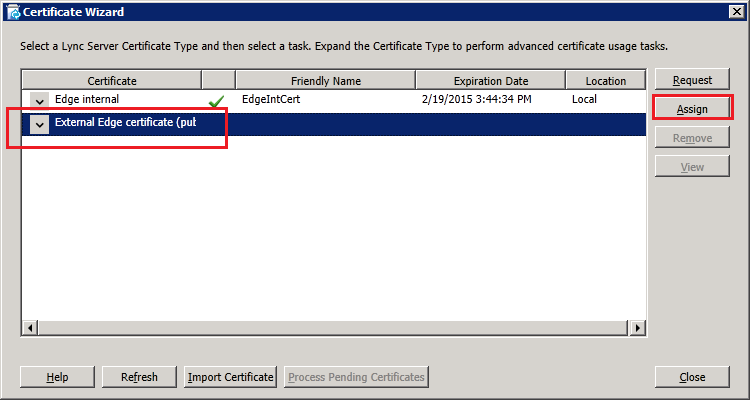
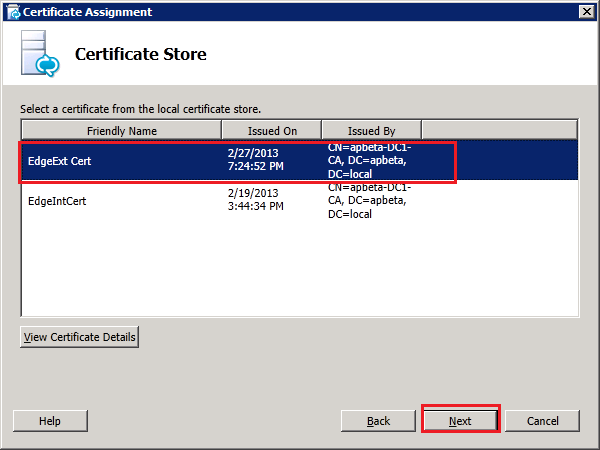
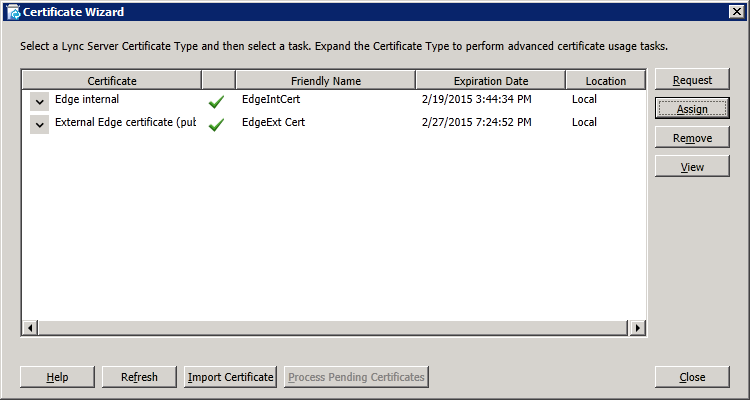
Step 4: Request and Assign Certificates for Edge
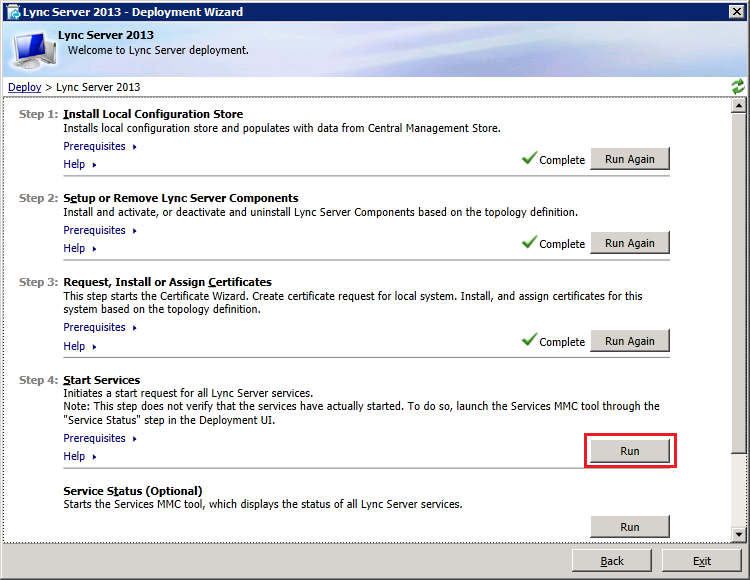
Step 5: Start Edge Services
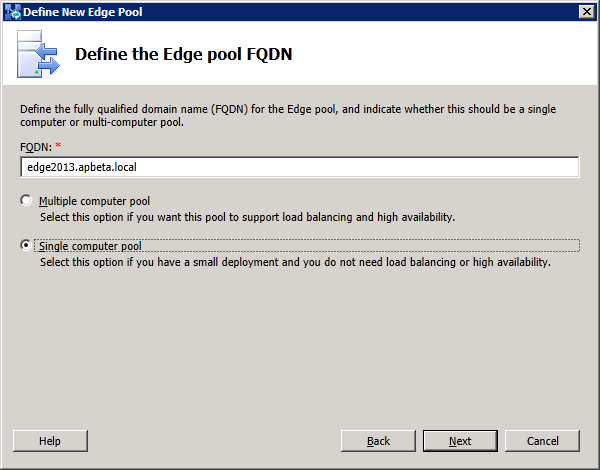
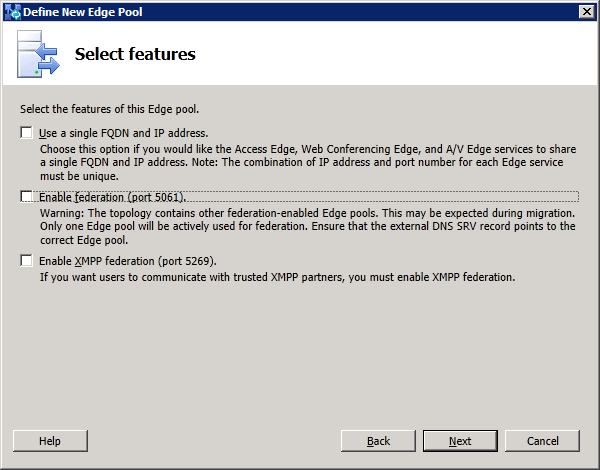
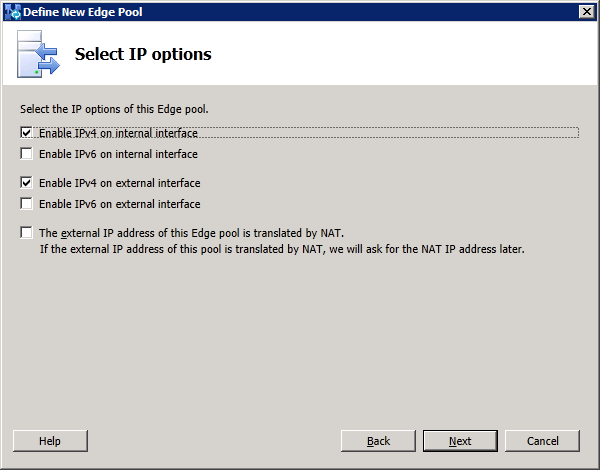
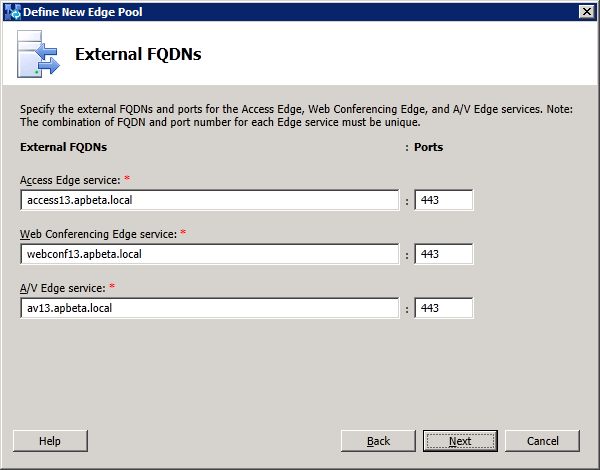
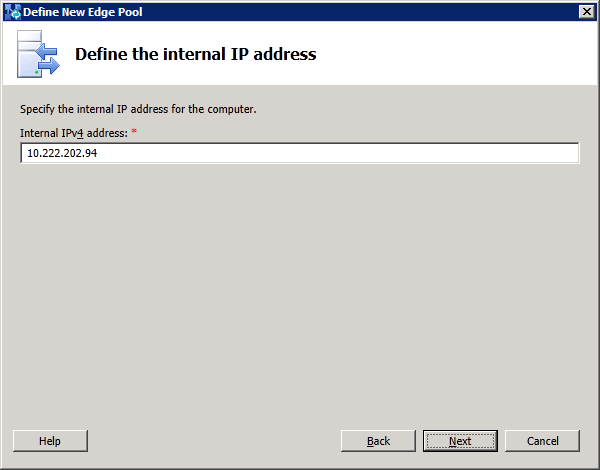
1. Define the new Edge pool in Topology Builder
node. Select "New Edge Pool..." to start defining the edge pool properties:
2. Install Prerequisite software for Lync2013 Edge
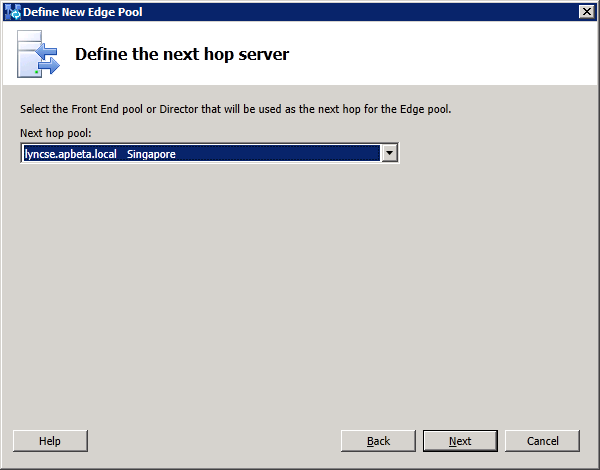
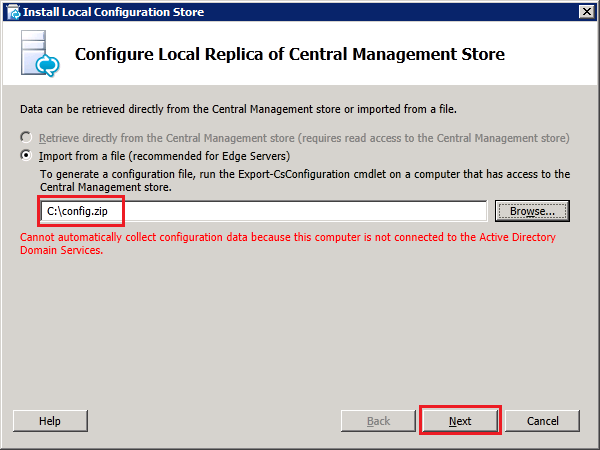
static routes on the internal interface to all internal networks where Lync clients or servers running Lync Server 2013 reside and edit the HOST file to contain a record for the next hop Lync2013 FE server which was configured as the Edge Server next hop address in Topology Builder.
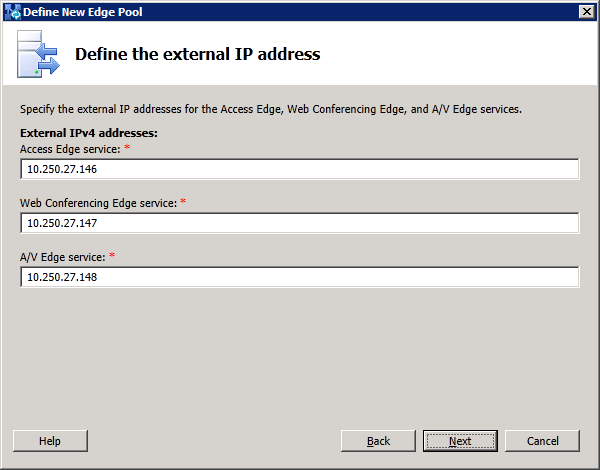
The other NIC card is for the external interface and we configure 3 IP address 10.250.27.[146-148]/26. The internal and external subnets must not be routable to each other. We also configure the default gateway on the external interface and would normally point to an
external DNS. Since we do not have a DNS server in the DMZ in our lab so we will use host files (shown later).
On the Windows2008R2 SP1 server, do the following in sequence:
1. Run Windows Update to get all the latest hotfixes and patches.
2. Install .NET Framework 4.5 from http://www.microsoft.com/en-us/download/details.aspx?id=30653
3. Enable Windows Powershell Integrated Scripting Envrionment (ISE) from Server Manager->Add Features
4. Install WMF3.0 from http://www.microsoft.com/en-us/download/details.aspx?id=34595 using the correct file. For Windows 2008R2 SP1 it should be Windows6.1-KB2506143-x64.msu
5. Install Windows Identity Foundation from http://go.microsoft.com/fwlink/p/?linkId=204657 using the correct file. For Windows 2008R2 SP1 it should be Windows6.1-KB974405-x64.msu
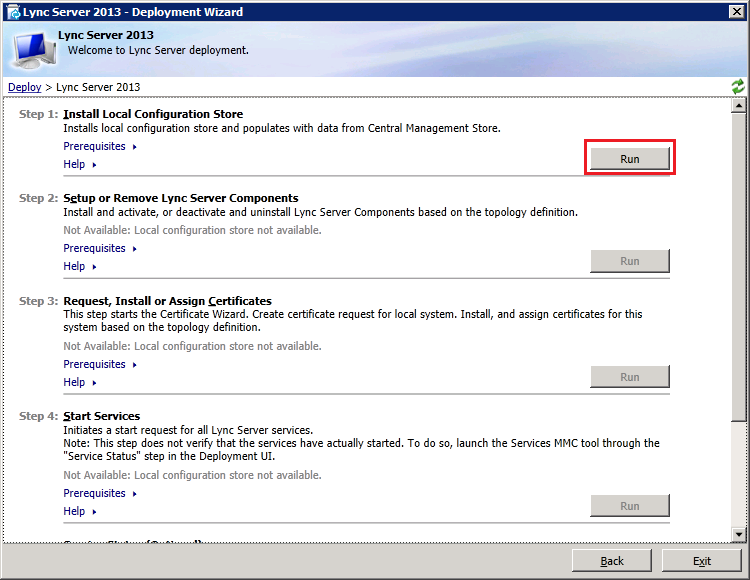
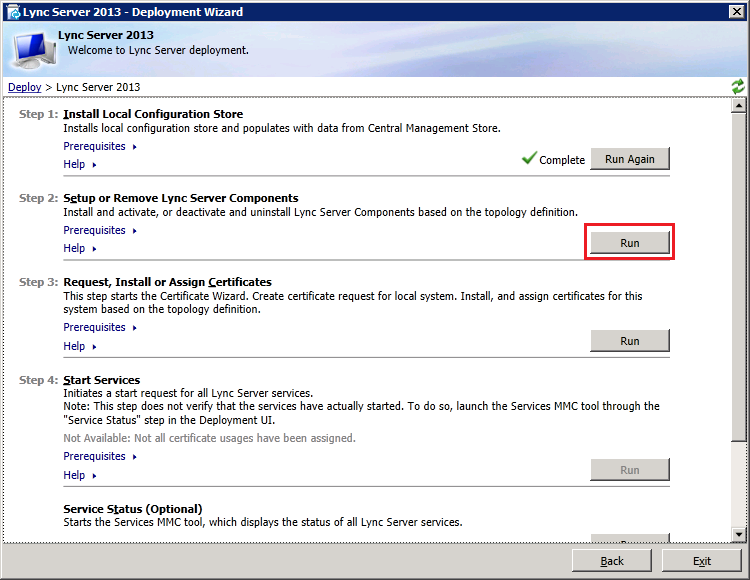
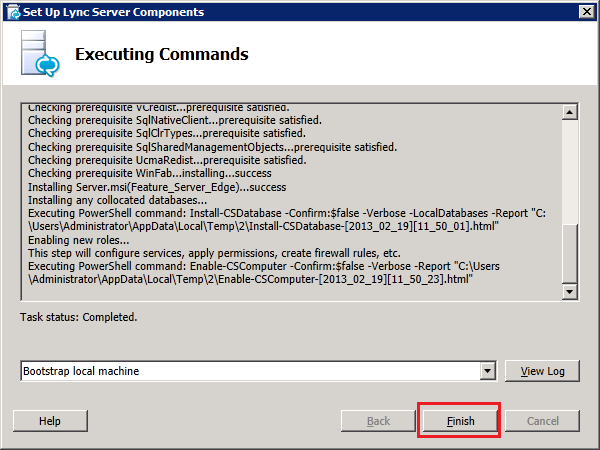
3: Deploy the Edge server components
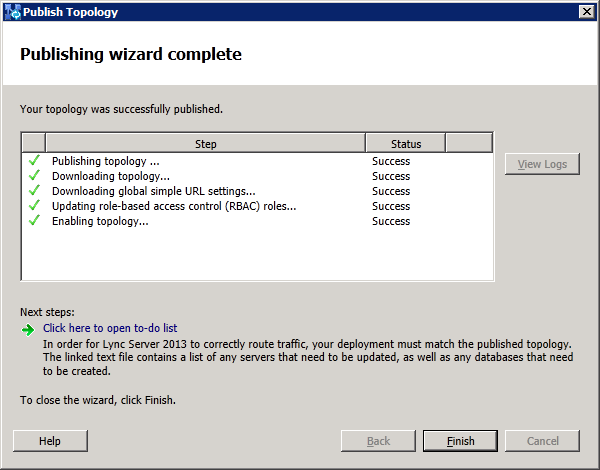
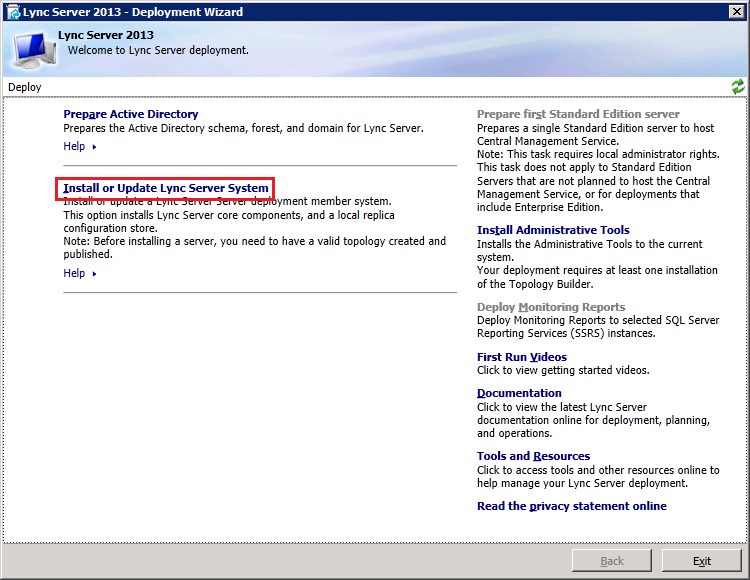
Now insert the Lync2013 Server installation DVD into the VM and double-click the icon to autorun the setup. Click Yes when prompted to install Microsoft Visual C++ Redistributable, In the next dialog box, accept the default Installation Location and click "Install". Accept the terms in the license agreement and click "OK" to proceed. In Deployment Wizard click "Install or Update Lync Server System"


 RSS Feed
RSS Feed