| Microsoft Teams Room on Android devices have been growing rapidly since its debut by Poly with the Studio X30/X50. While its relatively simple to deploy these devices, there are several considerations to ensure the devices can sign-in to the tenant especially when there are AzureAD and MEM/Intune security restrictions. This blogpost discusses in detail some of these considerations and how to identify and resolve possible issues. |
|
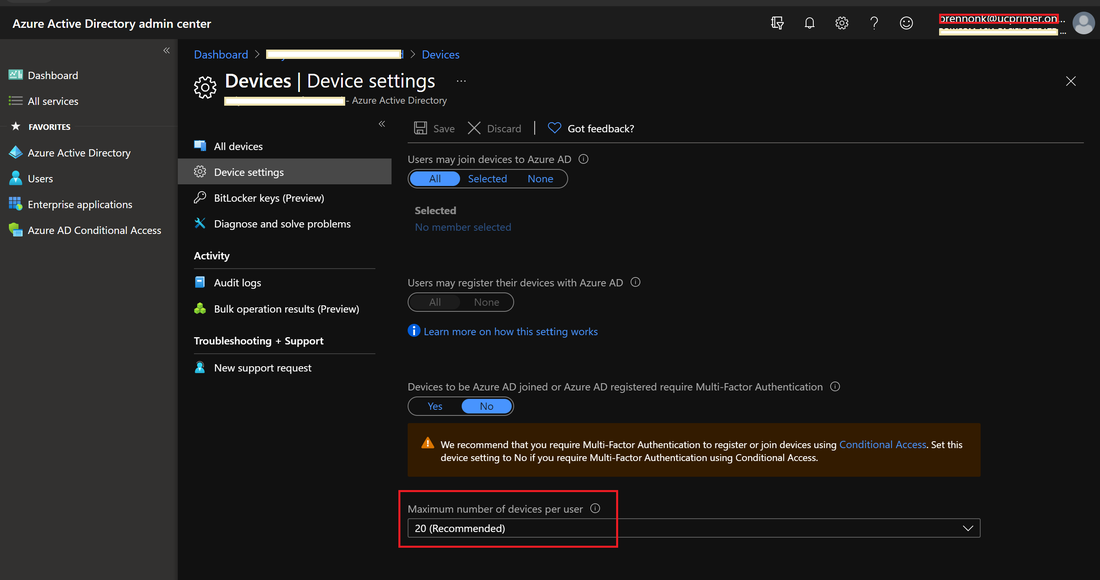
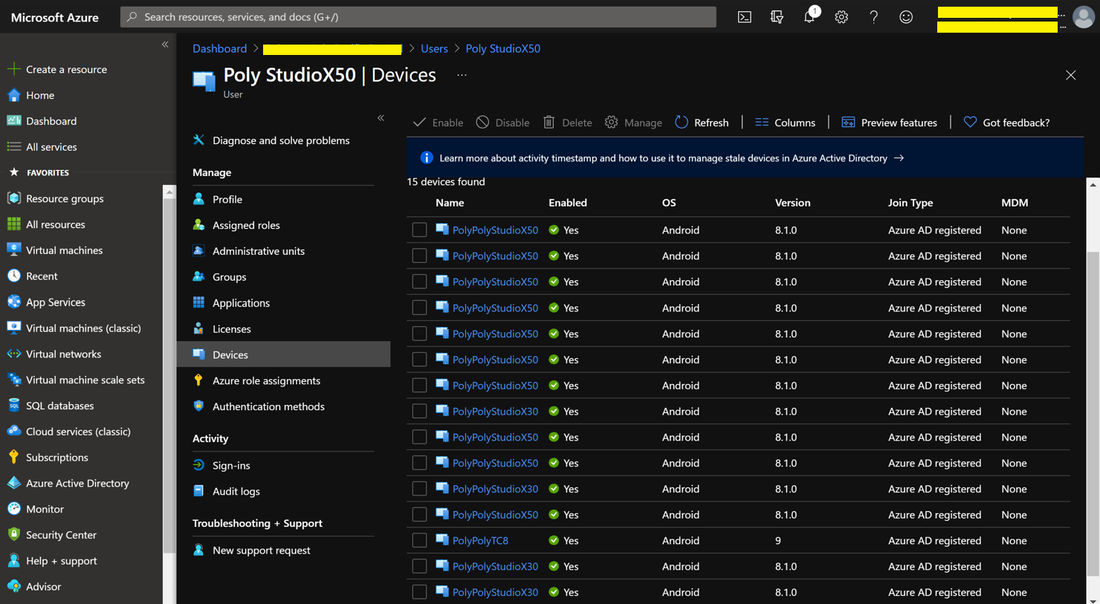
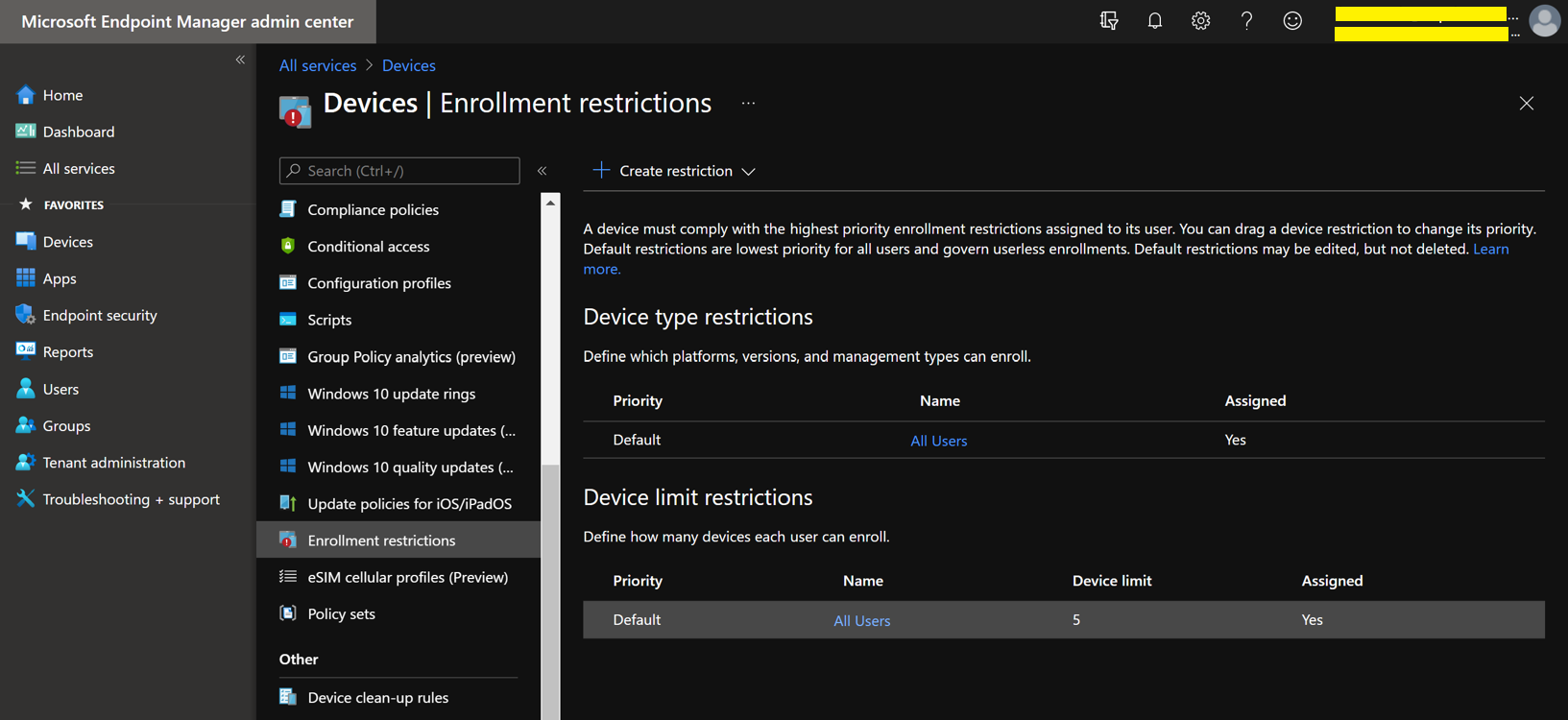
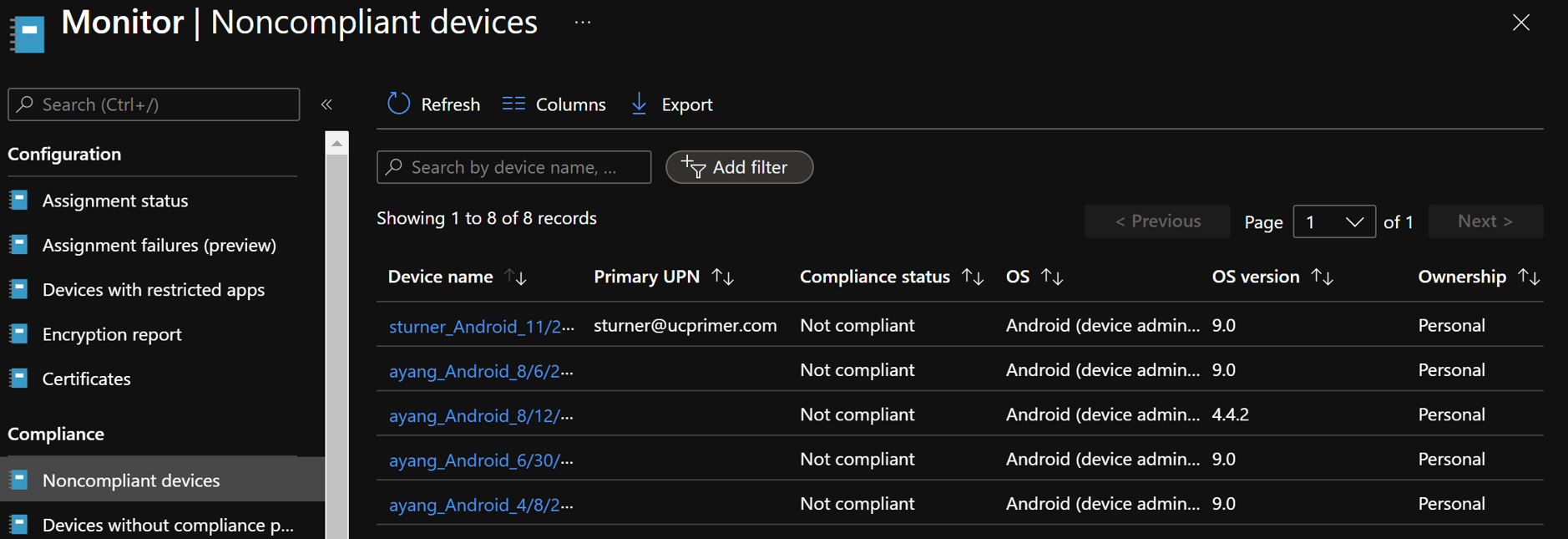
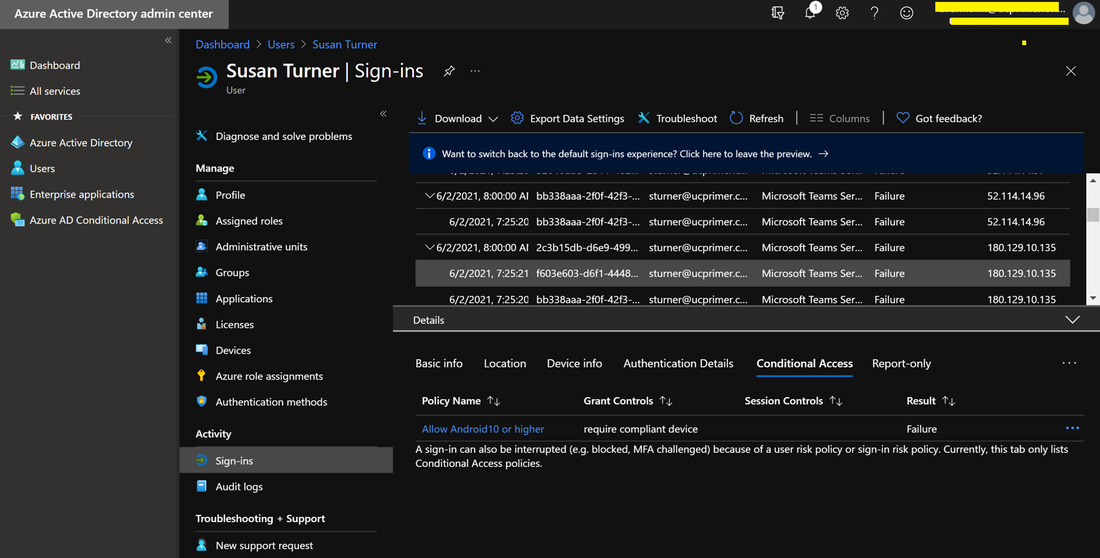
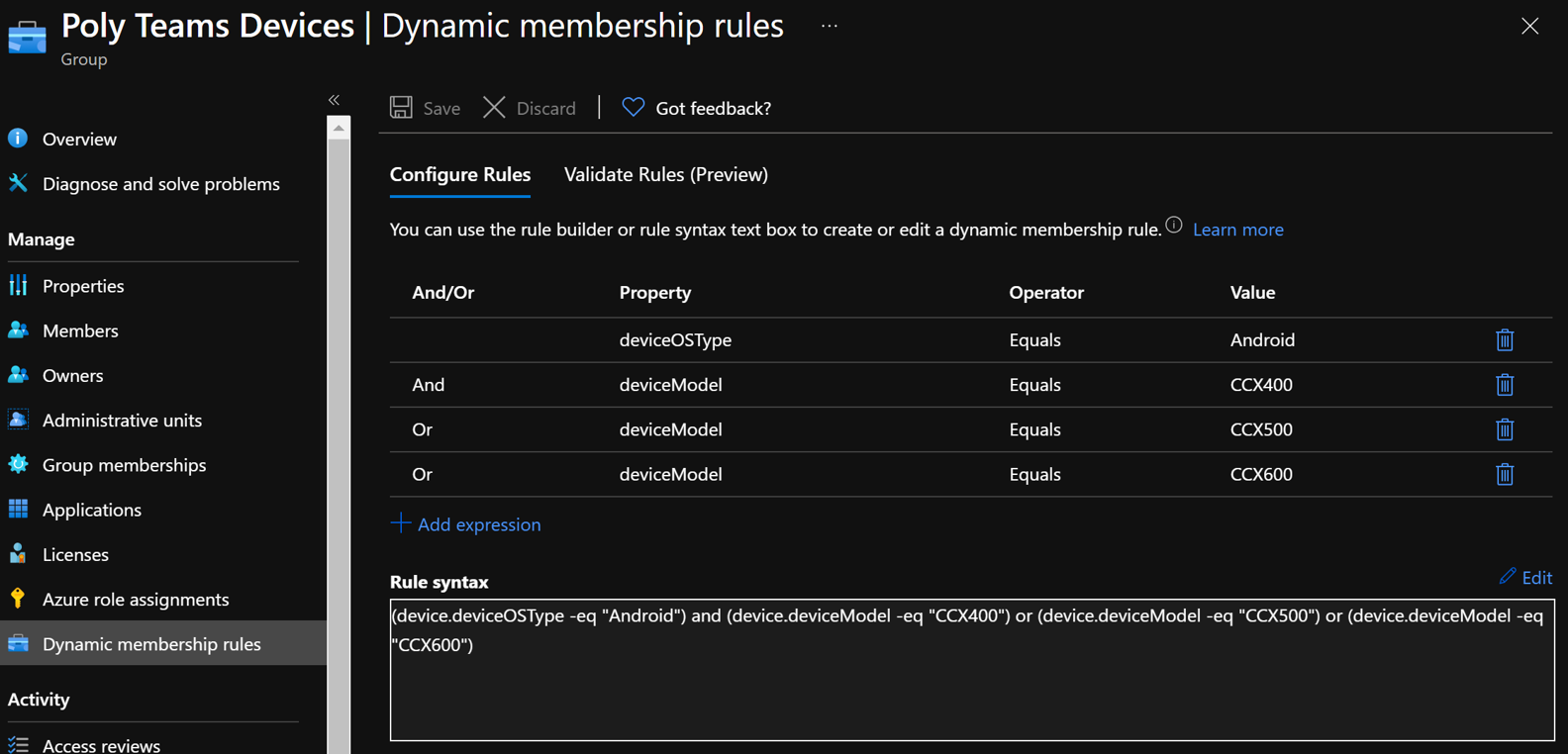
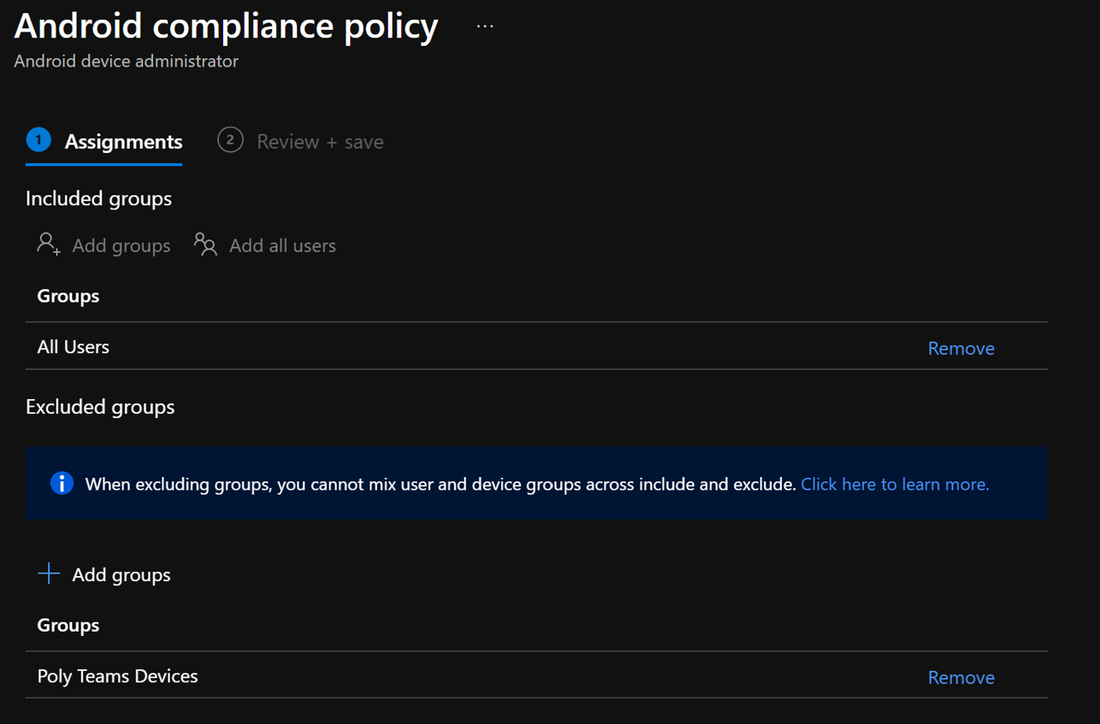
When using the same account to sign into multiple MTRoA devices, do note that there is a default limit of 20 devices per account. Once this limit is reached, the additional devices will not be able to sign-in using the same account. Its worth noting that should a device be factory reset and signed it again using the same account, this will count as an additional device registration. This default of 20 devices can be changed in AzureAD admin center as shown below but it is a tenant wide setting: To check whether an account has reached its limit, navigate to the account in AzureAD admin center and check the "Devices" section. For example, the diagram below shows an account that has 15 devices registered. If desired, simply select the devices and delete it to free up registrations. Do take care that this will cause any signed-in devices to be signed out. If an tenant has MEM/Intune enabled, then there are additional device enrollment limits on top of that in AzureAD. In fact, Intune/MEM's default is just 5 devices and while this can be changed, the maximum that can be configured is 15: Organizations also typically have Intune/MEM policies to secure Android smart phones signing into the tenant for email and Teams. Because MTRoA devices run the Android OS, they are also subject to the same policy restrictions. Hence its recommended to exclude MTRoA devices from these policies as they should not be treated the same as regular user smart phones. When a MTRoA device is unable to sign into Teams due to MEM/Intune policy restrictions, there aren't many error messages displayed on the device that indicates this. Once way to check if the device is indeed being blocked by Intune/MEM polices is to go to the MEM/Intune portal and navigate to the Compliance section under "Noncompliant devices". This will display all the accounts that have been marked non-compliant by MEM/Intune while signing-in to the tenant. Look for the MTRoA account that is being used and if it appears in this list, then its being blocked by policy: Once the MTRoA account is identified as being blocked by MEM/Intune, we need to know the actual policy setting that is causing the non-compliance. This can be found under the Users section and navigating to "Sign-ins". A list of failures will be displayed in the upper section, and in the details section below, there are several tabs can may indicate the reason for failures. For example. the picture below shows that a device failed a compliance policy that requires Android10 or higher OS: As mentioned earlier, MTRoA devices should be excluded from MEM/Intune policies created for regular user's smartphones. This can be done via first creating a Dynamic Group in AzureAD that will automatically include devices that match the deviceOSType property to "Android" and the "deviceModel" property to the device model name as shown below: Once the Dynamic Group is created, we can then assign this group to be excluded from the MEM/Intune policy as shown below: In conclusion, MTRoA devices are subject to the same MEM/Intune policies for regular user's Android smartphones and should be excluded from these policies as they are a entirely different category of devices.
0 Comments
Your comment will be posted after it is approved.
Leave a Reply. |
UCPrimerImportant LinksMicrosoft Teams Docs Archives
July 2024
Categories
All
This website uses marketing and tracking technologies. Opting out of this will opt you out of all cookies, except for those needed to run the website. Note that some products may not work as well without tracking cookies. Opt Out of Cookies |



 RSS Feed
RSS Feed