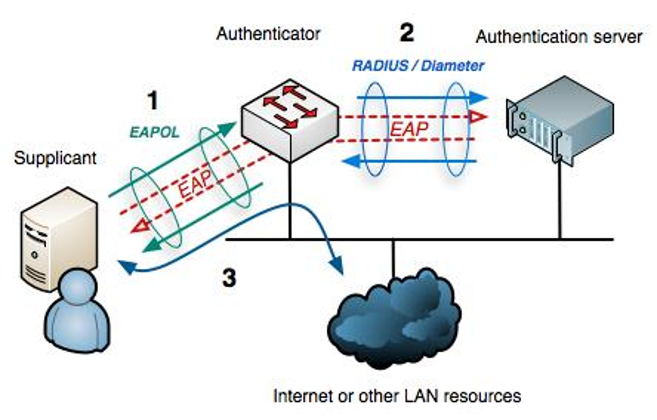
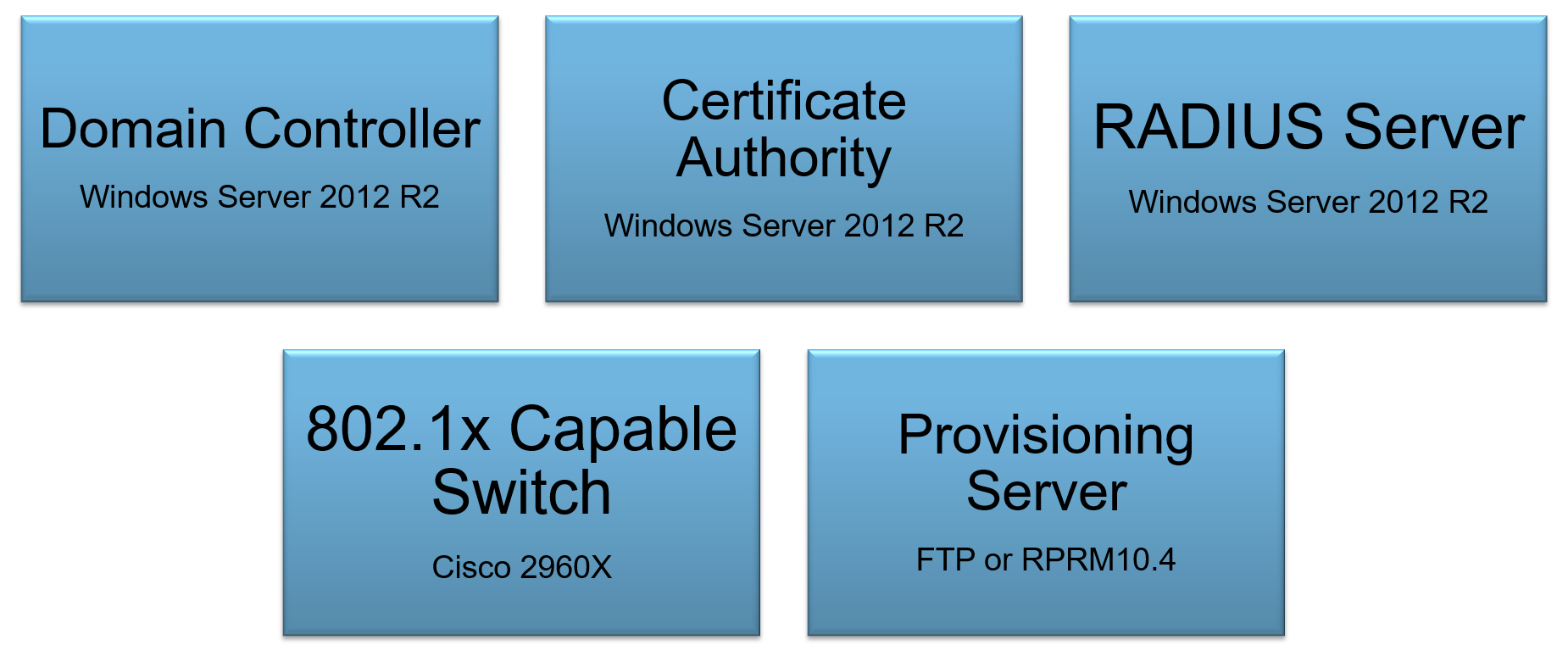
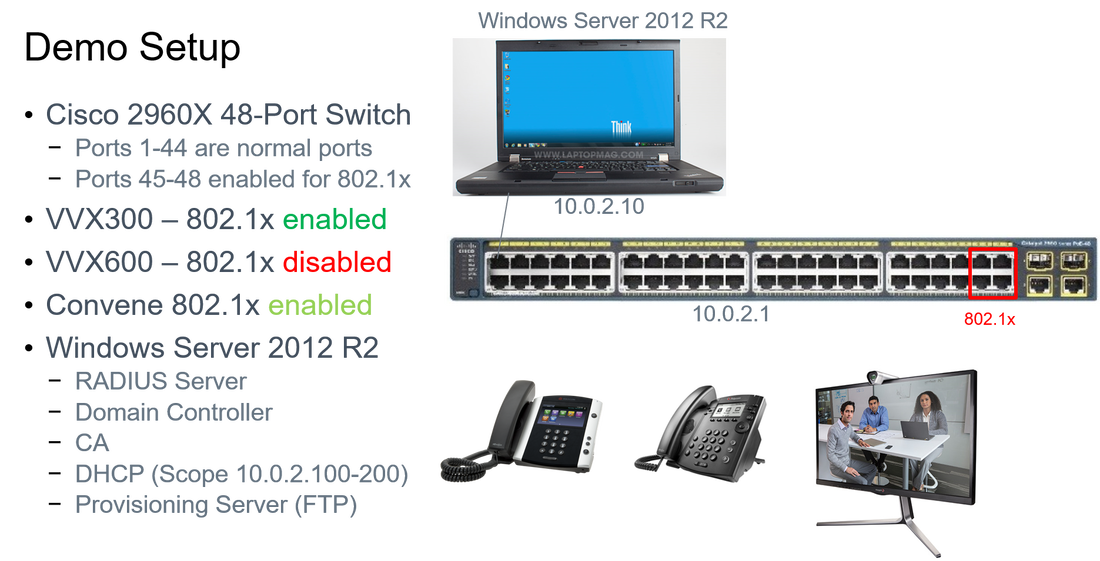
| The 802.1X protocol is an IEEE Standard for port-based Network Access Control and part of the IEEE 802.1 group of networking protocols. It provides an authentication mechanism to devices wishing to attach to a LAN or WLAN. Many organizations have already implemented 802.1x for PCs and laptops connecting to their enterprise network and many are now also mandating devices such as IP Phones and digital whiteboards to comply with 802.1x security standard. This blog post walks through how to setup 802.1x with EAP-TLS authentication on a Polycom VVX phone within a lab environment. Part 1 will focus on the overview, configuring the Cisco Switch and the Windows NPS RADIUS server. |
!
!
aaa authentication dot1x default group radius
aaa authorization network default group radius
dot1x system-auth-control
!
interface GigabitEthernet1/0/2 Gi1/0/48
switchport mode access
authentication port-control auto
authentication violation replace
dot1x pae authenticator
dot1x timeout quiet-period 10
dot1x timeout tx-period 3
dot1x timeout supp-timeout 10
dot1x max-req 10
dot1x max-reauth-req 1
spanning-tree portfast
!
radius server DC01
address ipv4 10.0.2.10 auth-port 1645 acct-port 1646
key <yoursharedsecret>
Using 4244 out of 524288 bytes
!
! No configuration change since last restart
! NVRAM config last updated at 02:56:04 UTC Thu Jan 5 2017
!
version 15.0
no service pad
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname Cisco2960
!
boot-start-marker
boot-end-marker
!
enable secret 5 xxxxxxxxxxxxxxxxxxxxxxxxxxxx
!
username xxxxxxxxxx password 0 xxxxxxxxxxx
aaa new-model
!
!
aaa authentication dot1x default group radius
aaa authorization network default group radius
!
!
!
!
!
!
aaa session-id common
clock timezone UTC 8 0
switch 1 provision ws-c2960x-48ts-l
!
!
!
!
crypto pki trustpoint TP-self-signed-2291087104
enrollment selfsigned
subject-name cn=IOS-Self-Signed-Certificate-2291087104
revocation-check none
rsakeypair TP-self-signed-2291087104
!
!
crypto pki certificate chain TP-self-signed-2291087104
certificate self-signed 01 nvram:IOS-Self-Sig#1.cer
dot1x system-auth-control
spanning-tree mode pvst
spanning-tree extend system-id
!
!
!
!
!
!
vlan internal allocation policy ascending
!
!
!
!
!
!
interface FastEthernet0
no ip address
!
interface GigabitEthernet1/0/1
!
interface GigabitEthernet1/0/2
!
............<Lines removed for brevity>............
interface GigabitEthernet1/0/44
!
interface GigabitEthernet1/0/45
switchport mode access
authentication port-control auto
authentication violation replace
dot1x pae authenticator
dot1x timeout quiet-period 10
dot1x timeout tx-period 3
dot1x timeout supp-timeout 10
dot1x max-req 10
dot1x max-reauth-req 1
spanning-tree portfast
!
interface GigabitEthernet1/0/46
switchport mode access
authentication port-control auto
authentication violation replace
dot1x pae authenticator
dot1x timeout quiet-period 10
dot1x timeout tx-period 3
dot1x timeout supp-timeout 10
dot1x max-req 10
dot1x max-reauth-req 1
spanning-tree portfast
!
interface GigabitEthernet1/0/47
switchport mode access
authentication port-control auto
authentication violation replace
dot1x pae authenticator
dot1x timeout quiet-period 10
dot1x timeout tx-period 3
dot1x timeout supp-timeout 10
dot1x max-req 10
dot1x max-reauth-req 1
spanning-tree portfast
!
interface GigabitEthernet1/0/48
switchport mode access
authentication port-control auto
authentication violation replace
dot1x pae authenticator
dot1x timeout quiet-period 10
dot1x timeout tx-period 3
dot1x timeout supp-timeout 10
dot1x max-req 10
dot1x max-reauth-req 3
spanning-tree portfast
!
interface GigabitEthernet1/0/49
!
interface GigabitEthernet1/0/50
!
interface GigabitEthernet1/0/51
!
interface GigabitEthernet1/0/52
!
interface Vlan1
ip address 10.0.2.1 255.255.255.0
!
ip default-gateway 10.0.2.254
ip http server
ip http secure-server
!
!
!
!
radius server dcrad
address ipv4 10.0.2.10 auth-port 1645 acct-port 1646
key <yoursharedsecret>
!
!
!
line con 0
line vty 0 4
password xxxxxxxxxxx
line vty 5 15
password xxxxxxxxxxx
!
end
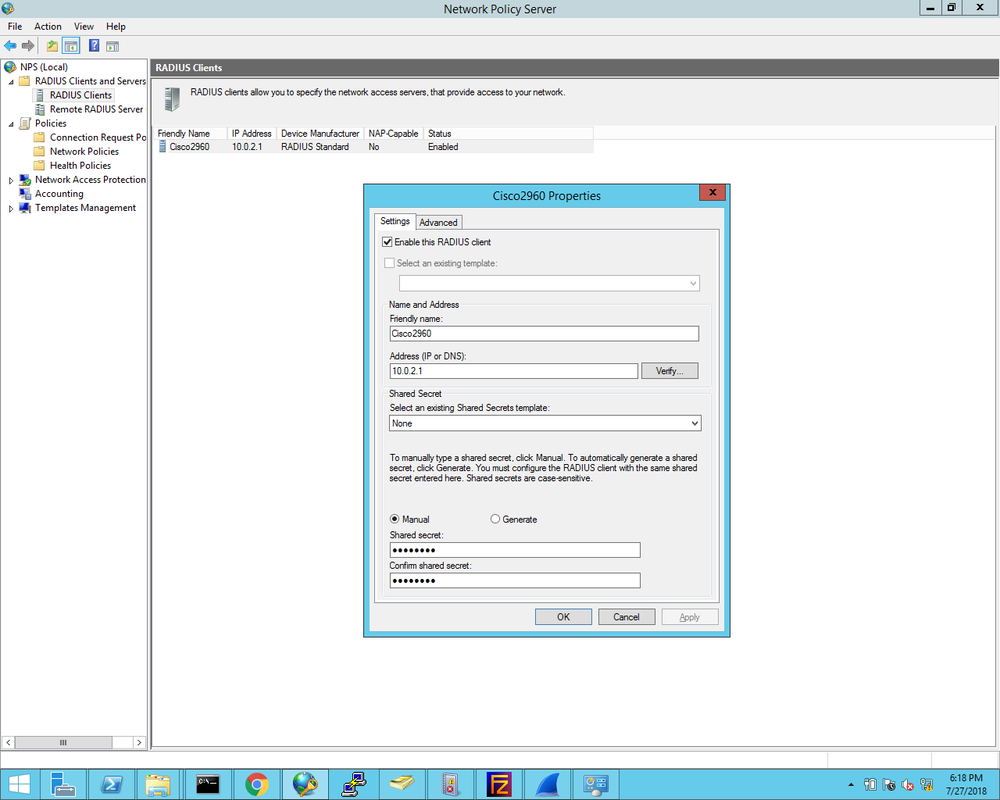
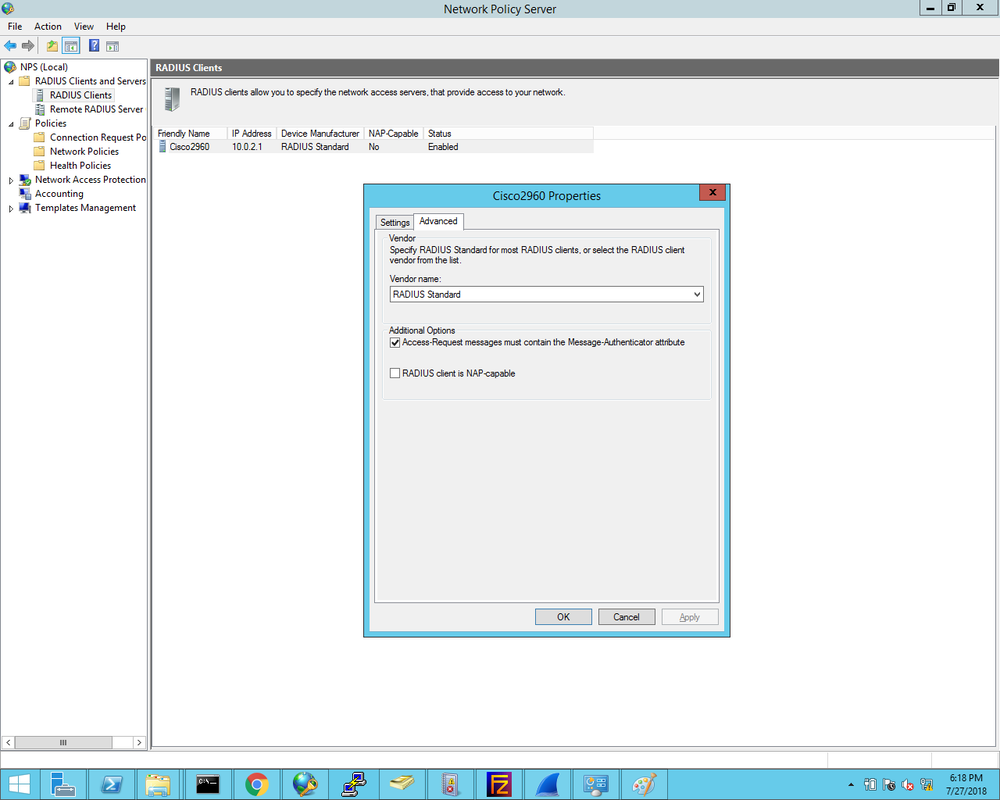
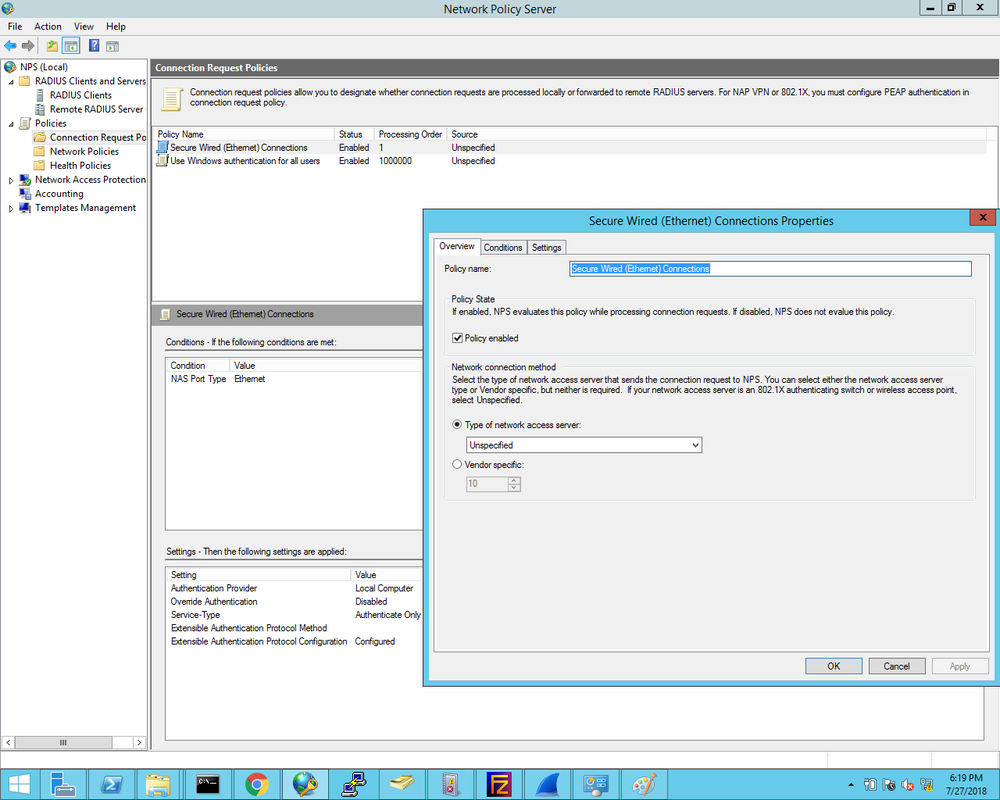
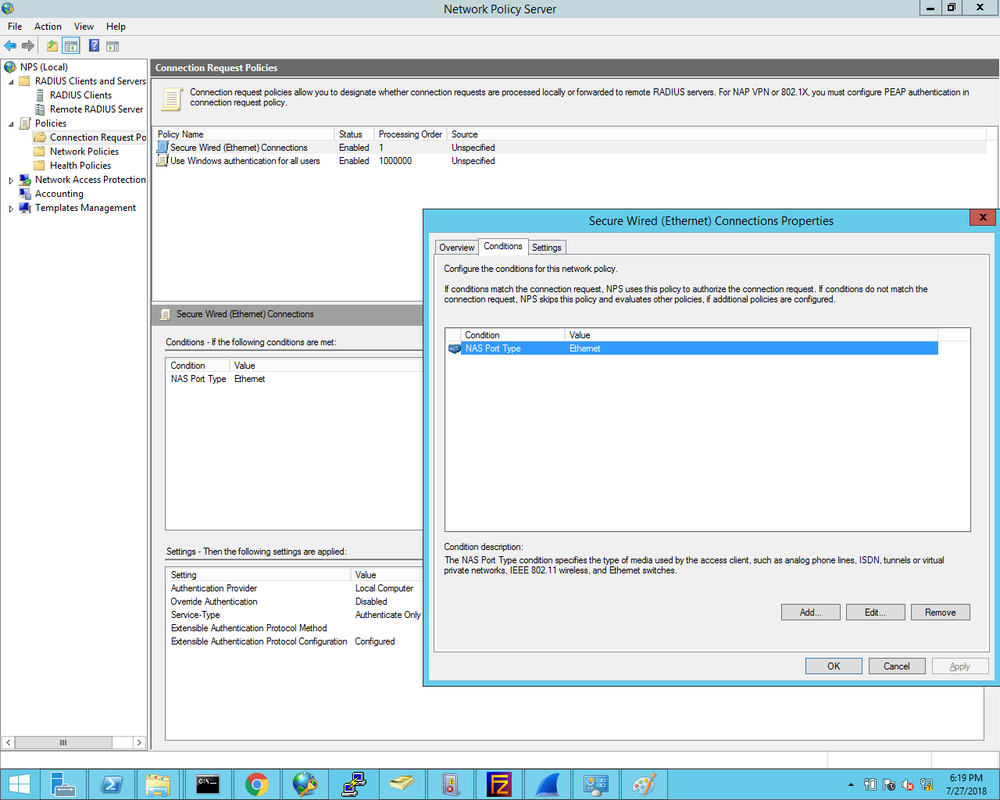
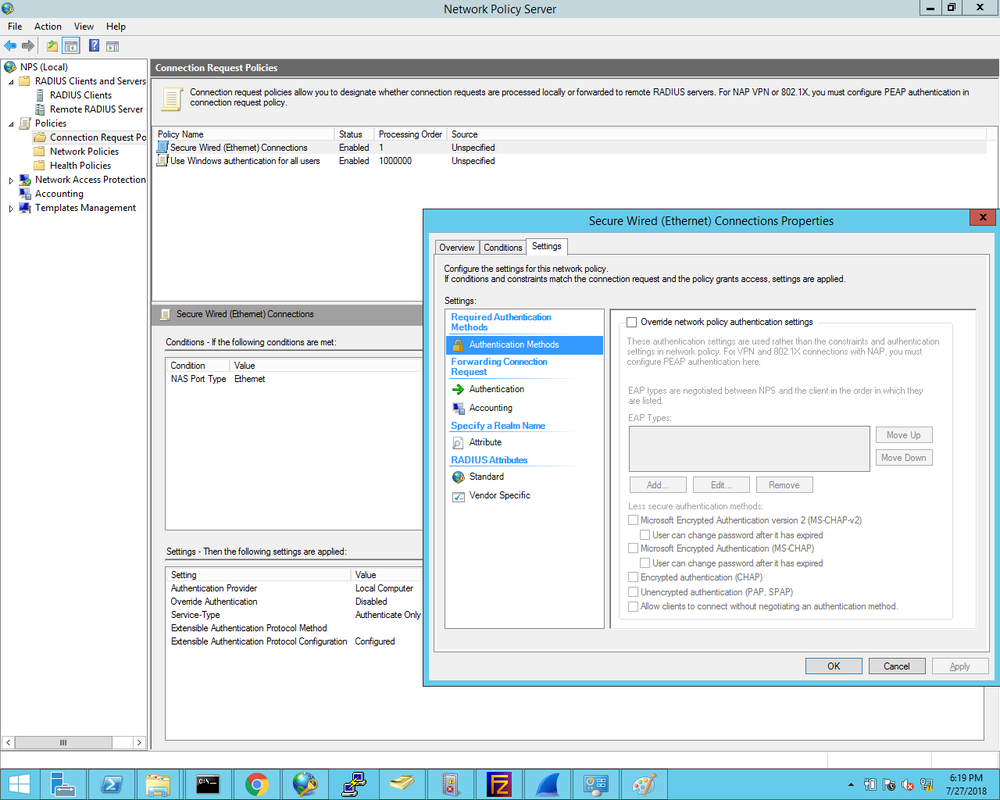
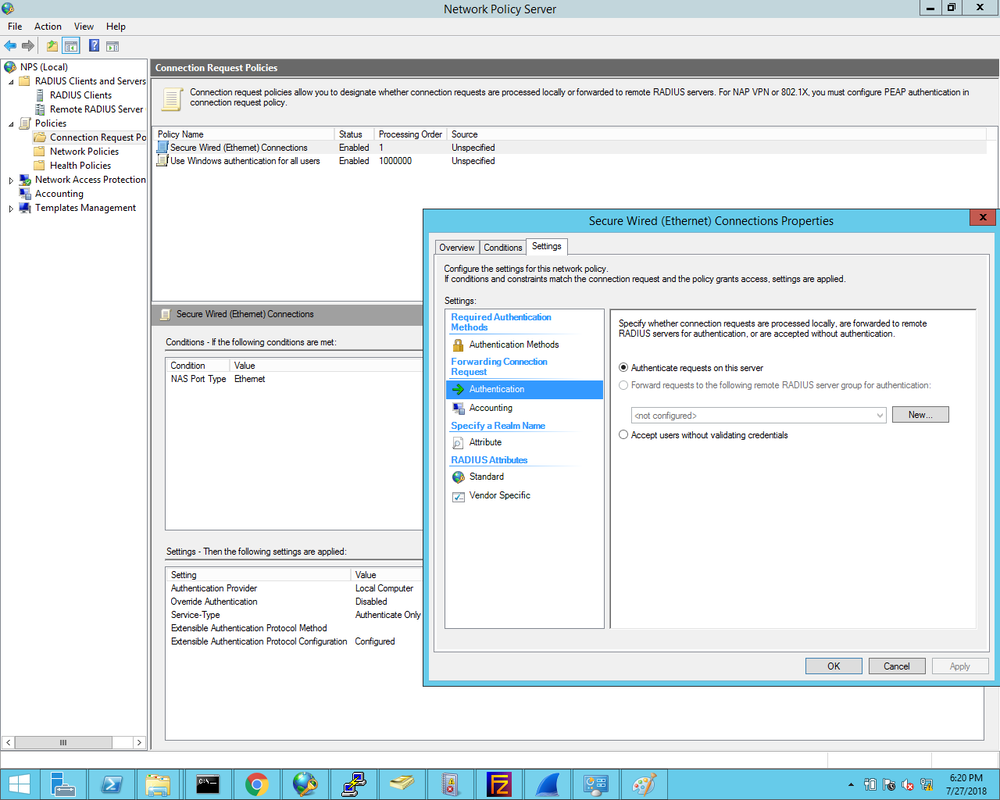
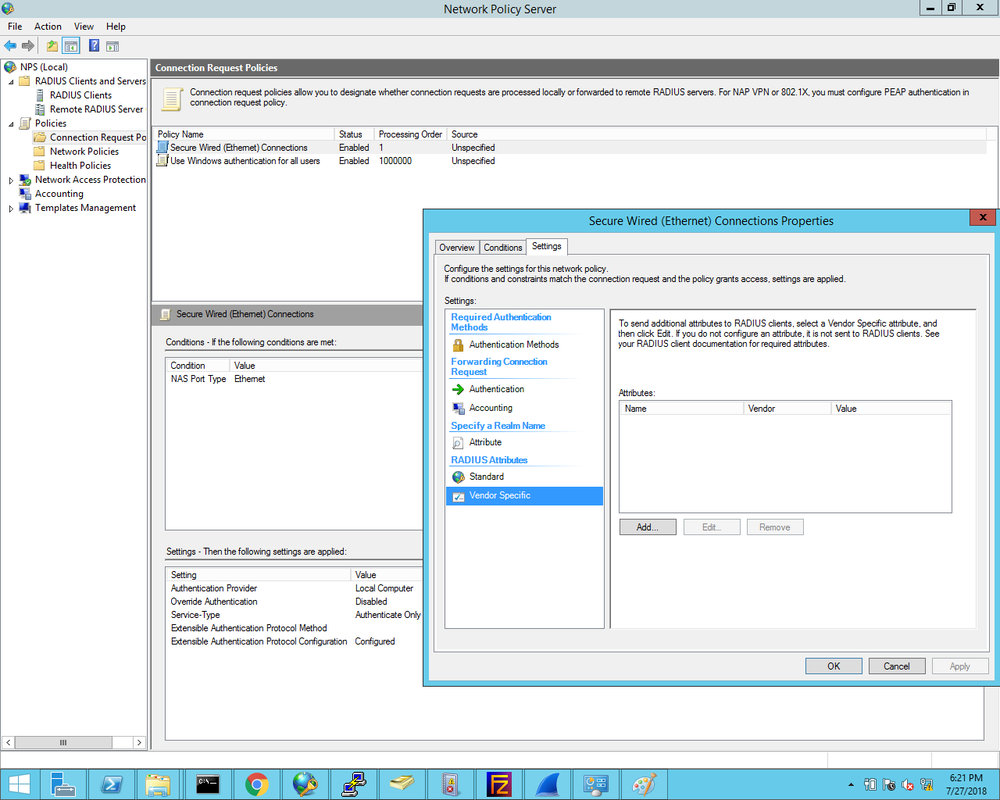
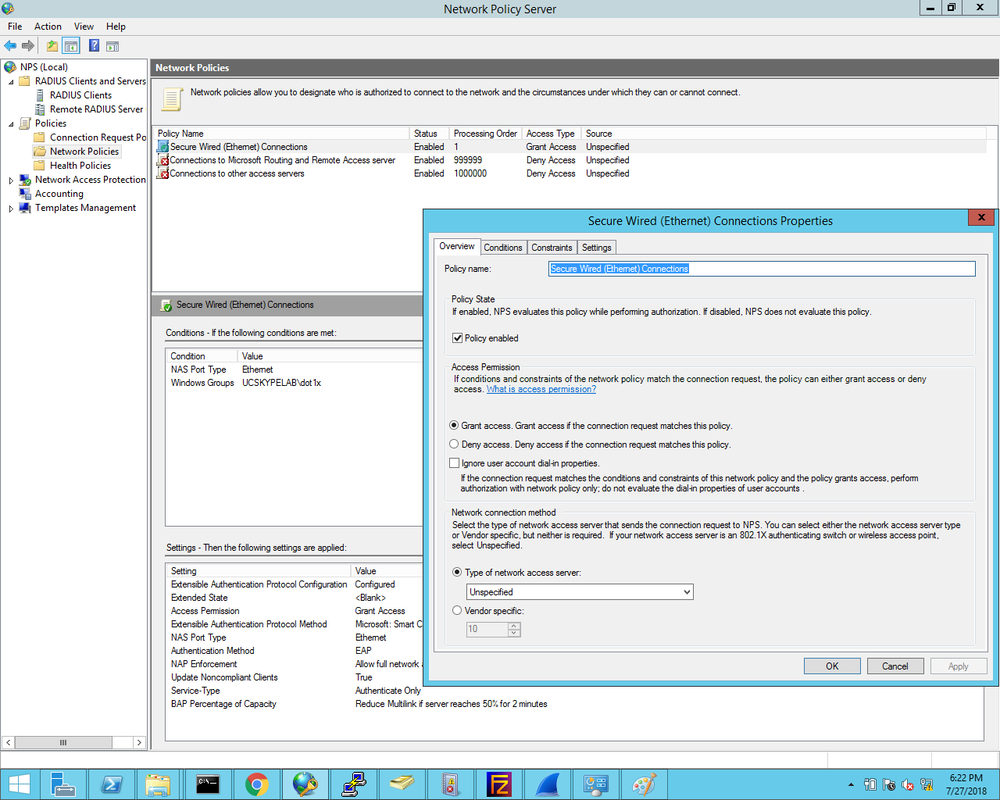
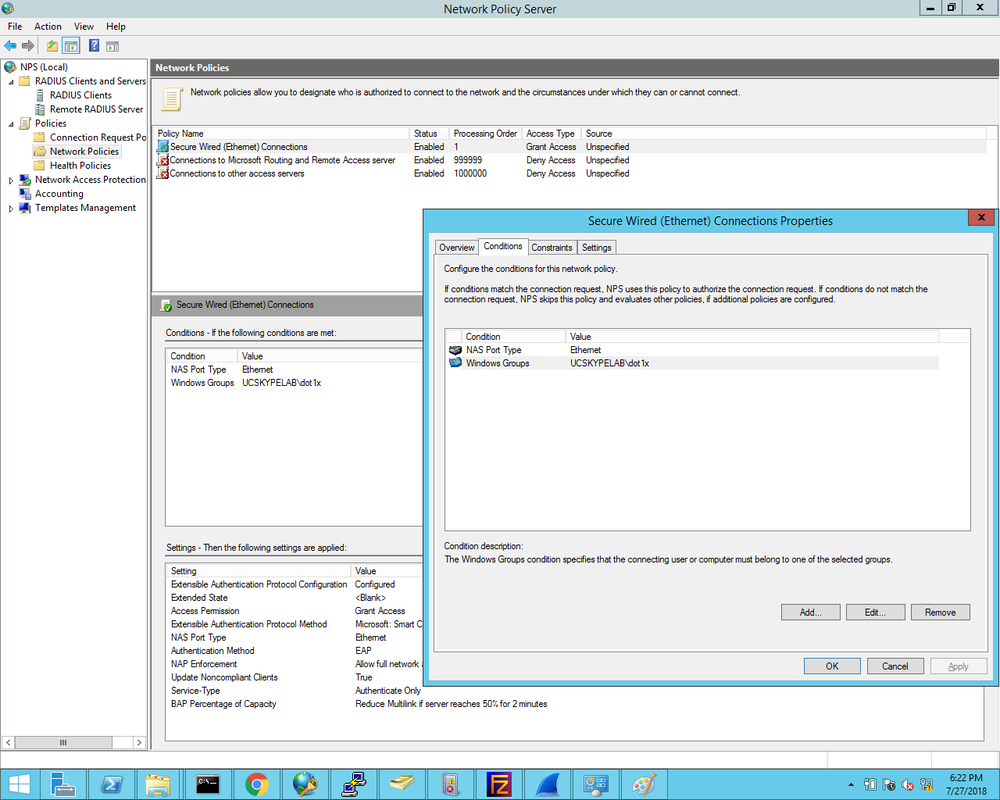
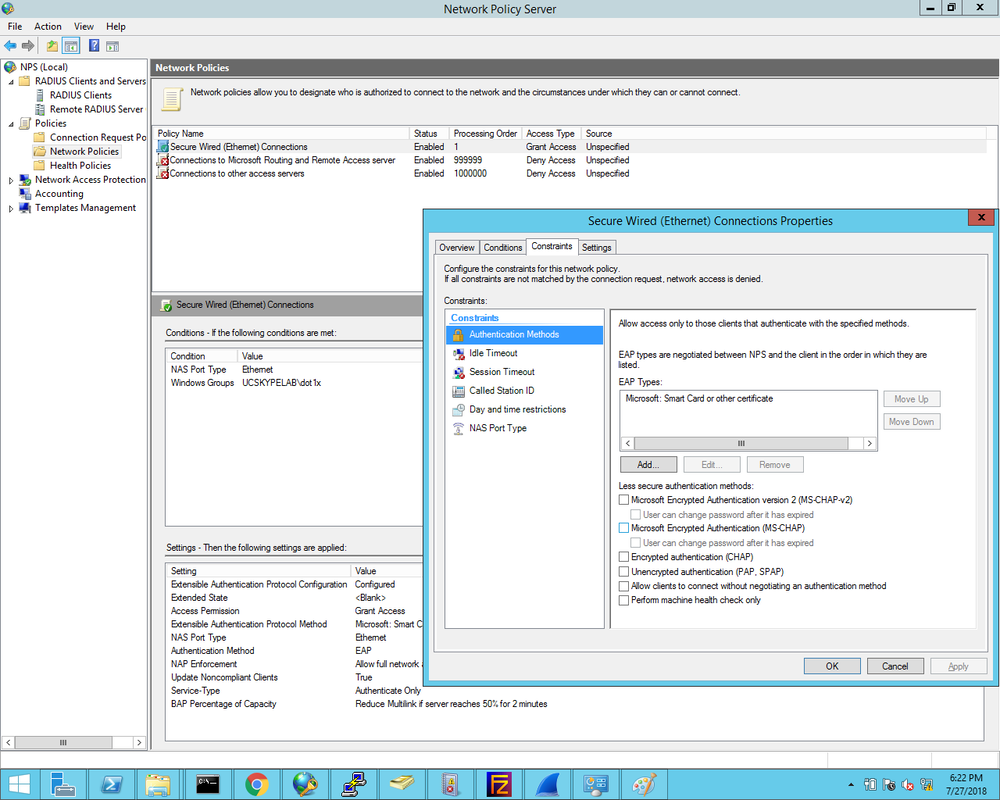
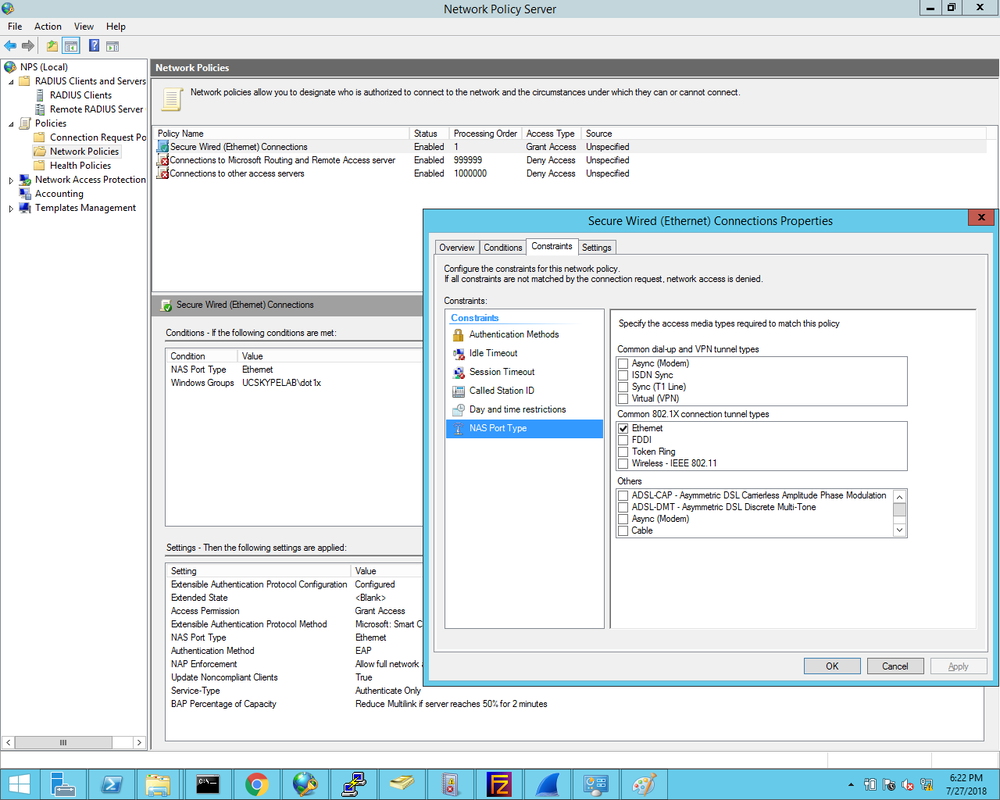
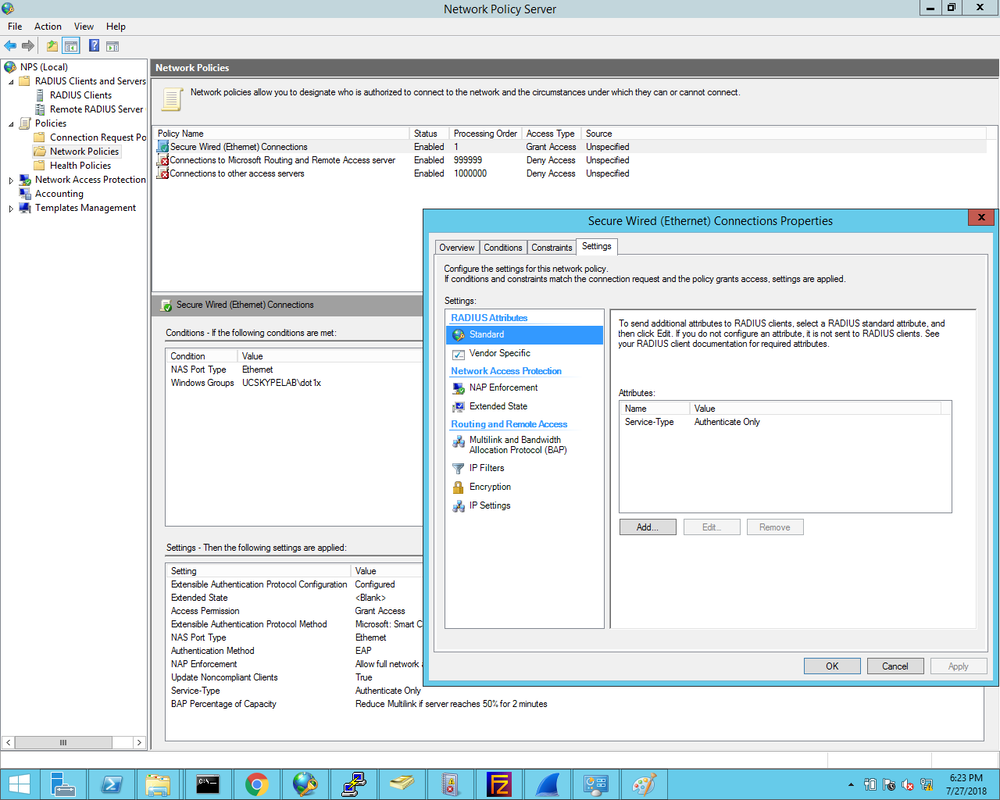
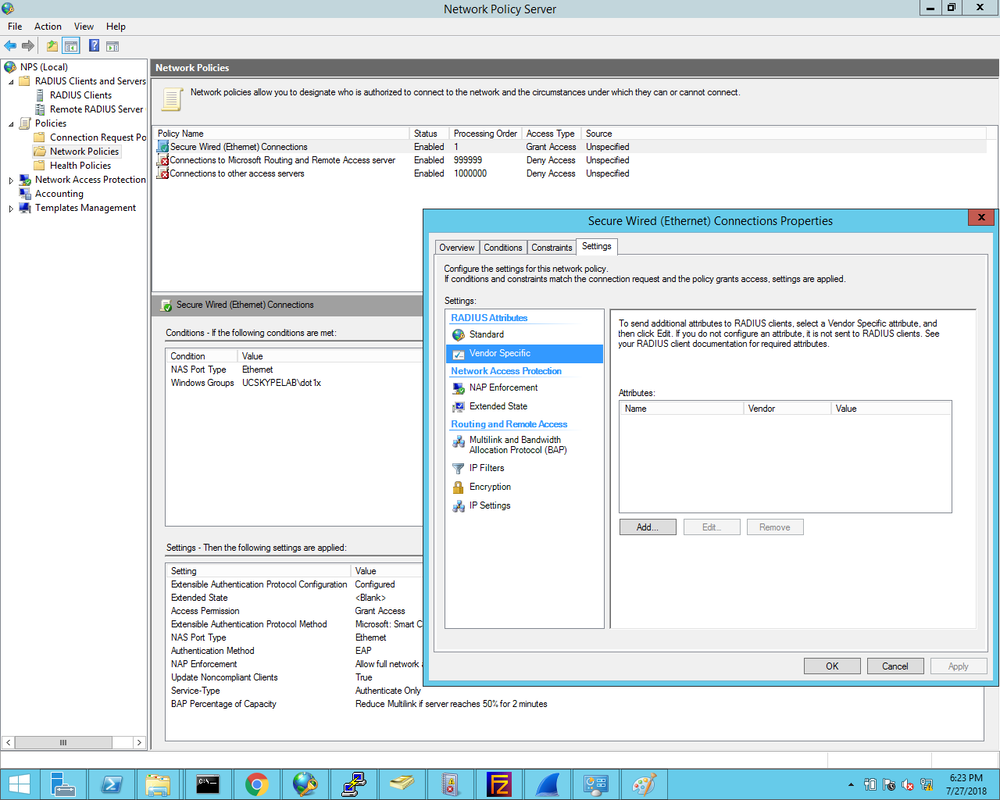
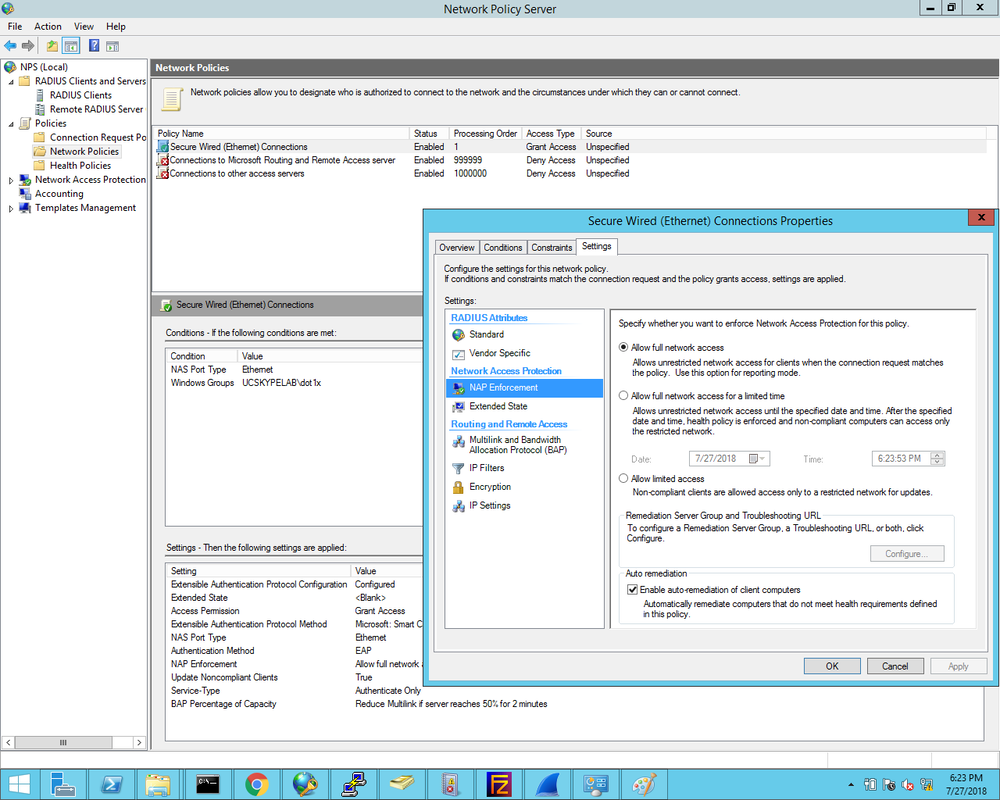
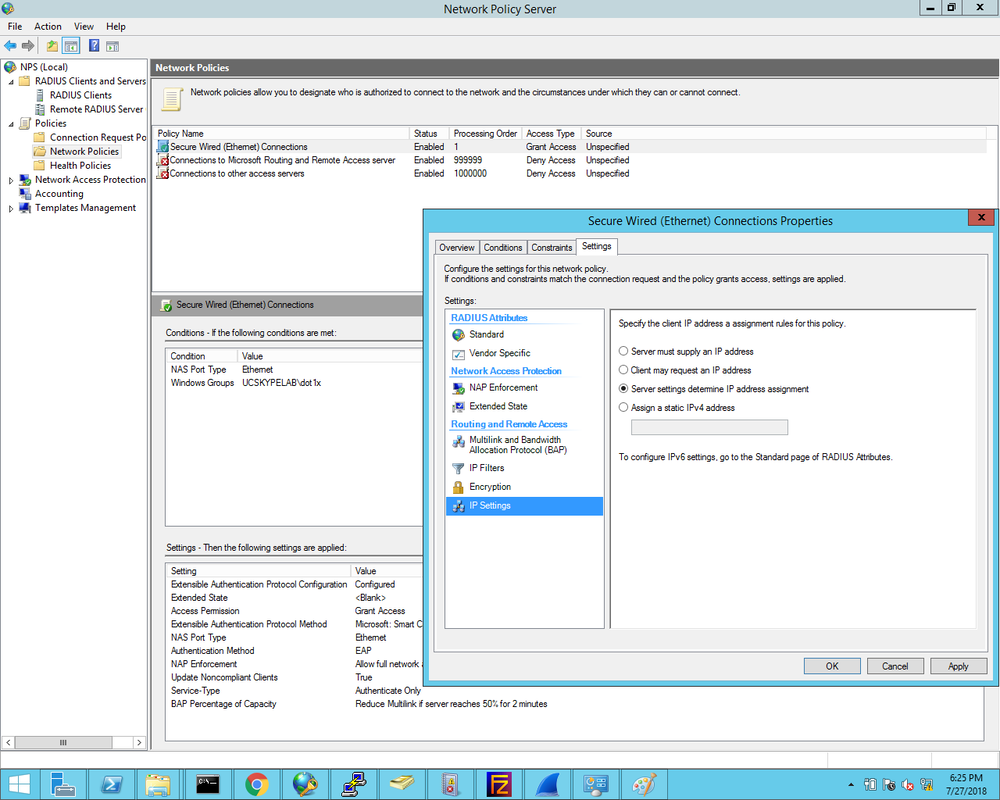
1. First we define the Cisco2960X switch as the Radius client and enter the Shared Secret that was configured on the switch earlier:



 RSS Feed
RSS Feed