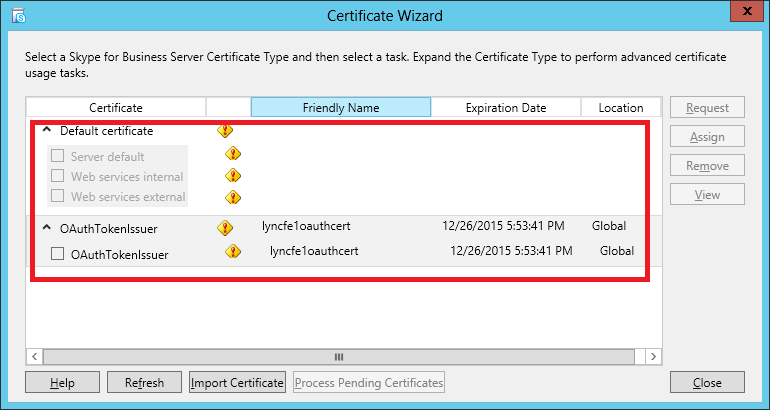
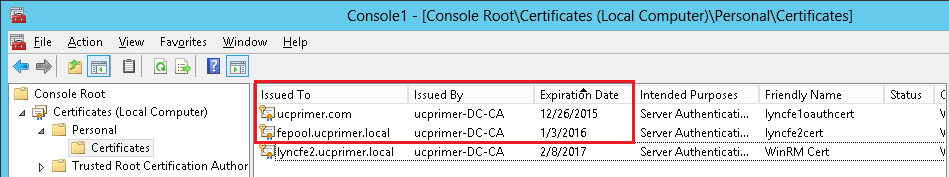
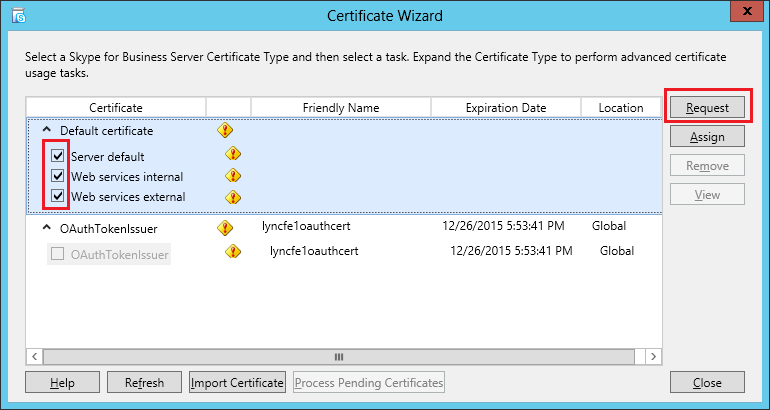
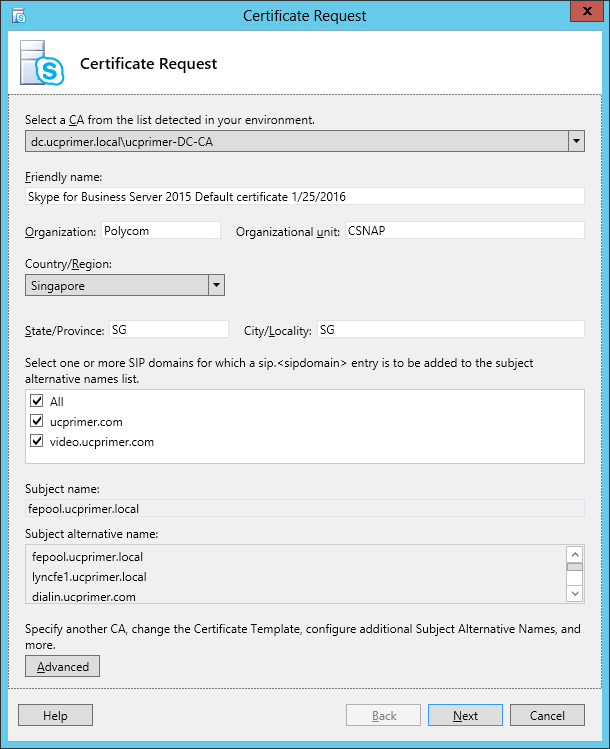
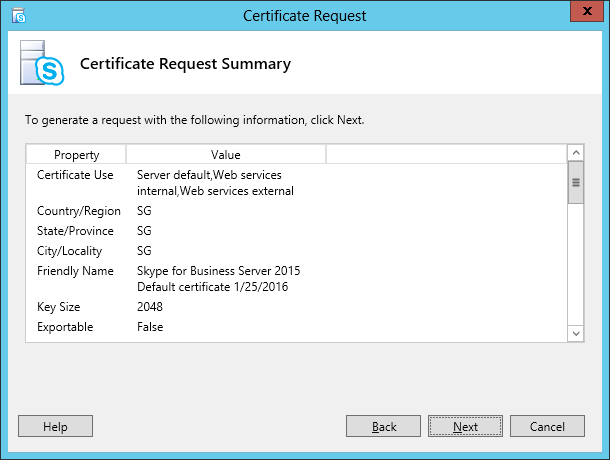
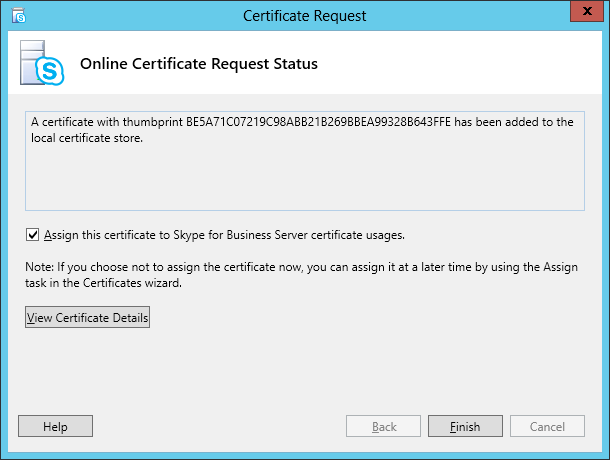
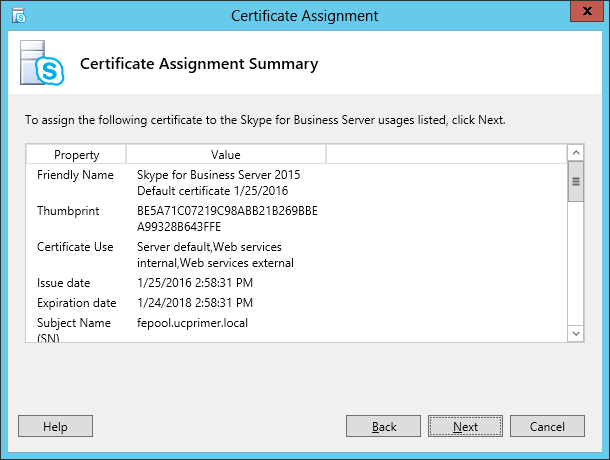
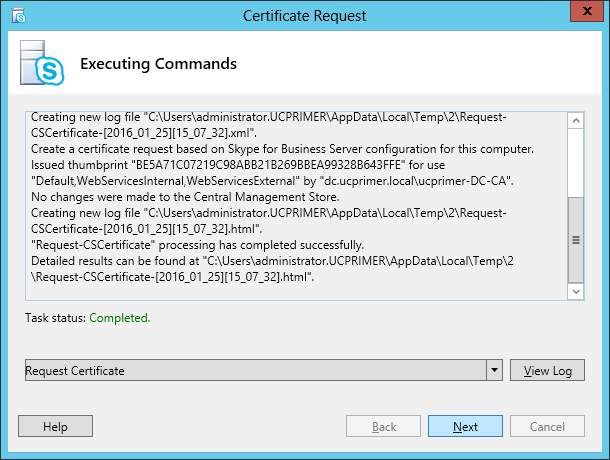
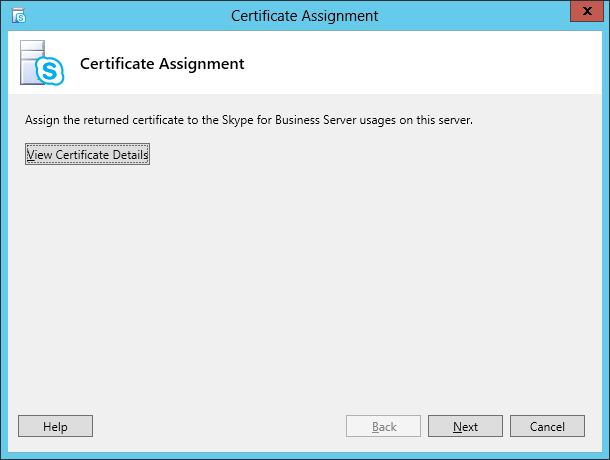
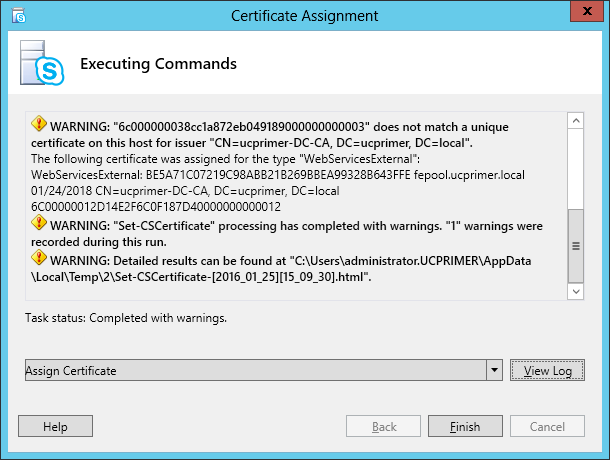
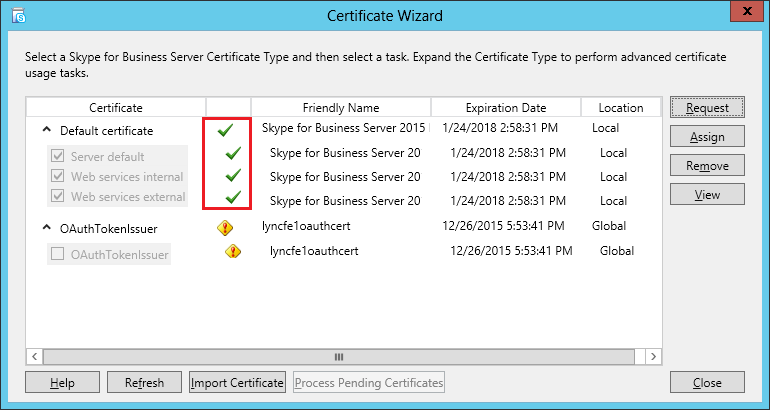
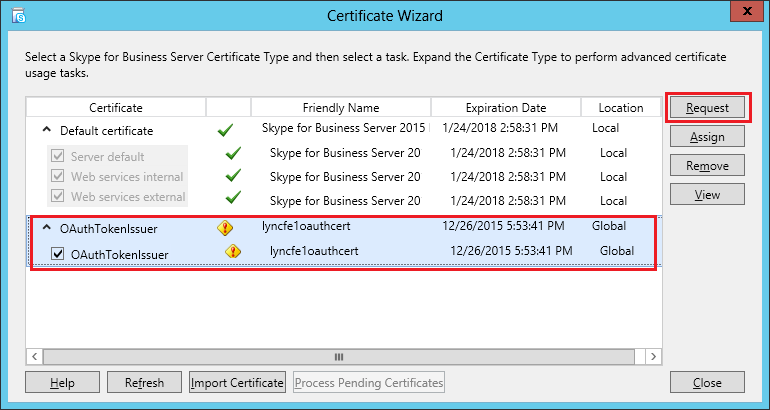
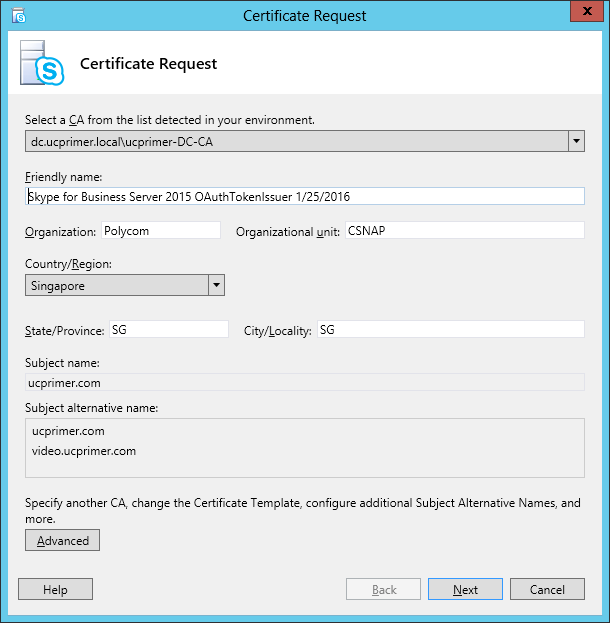
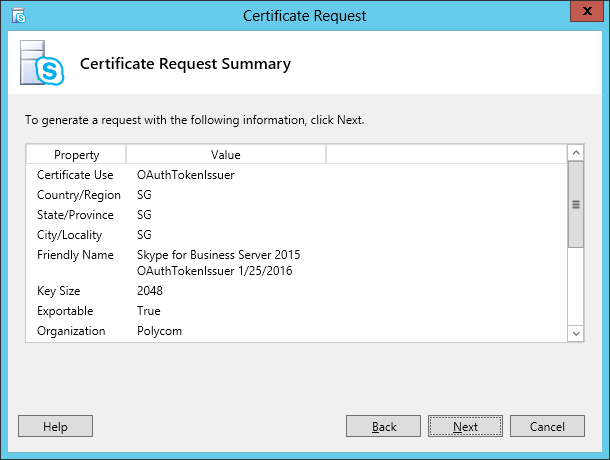
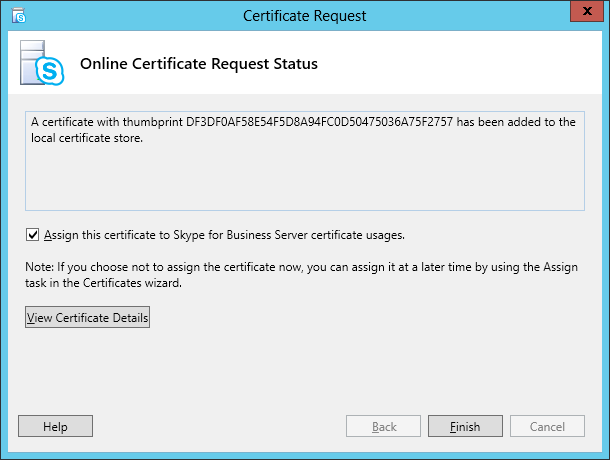
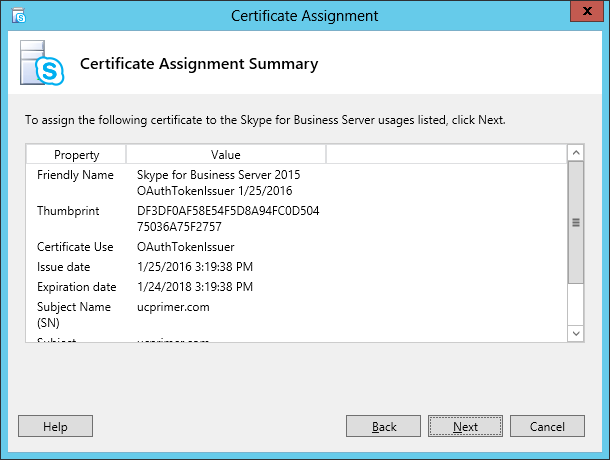
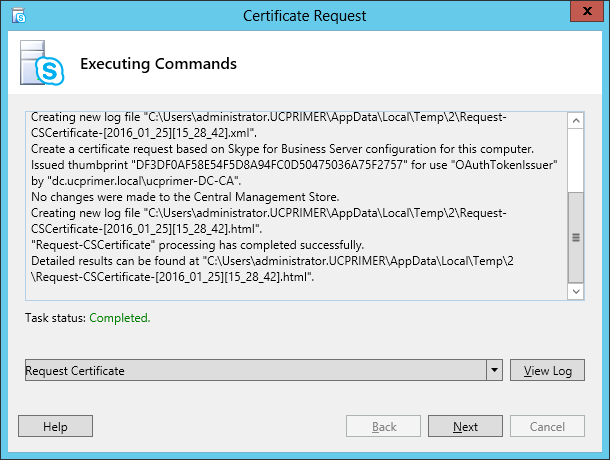
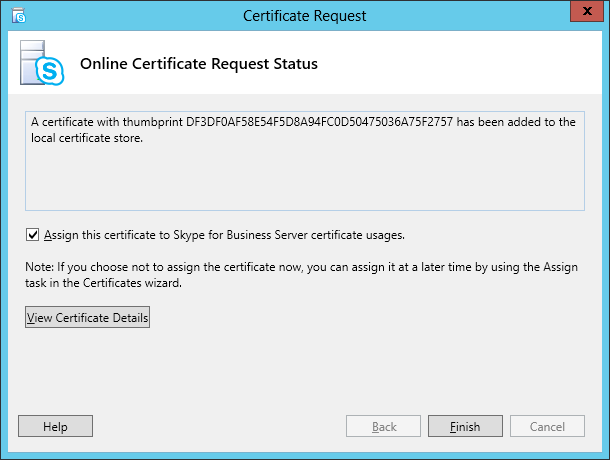
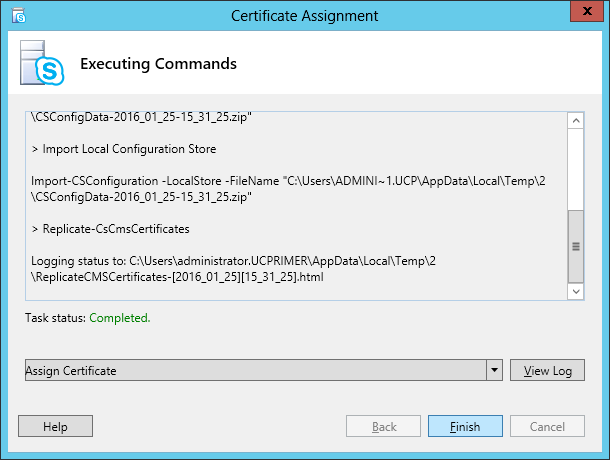
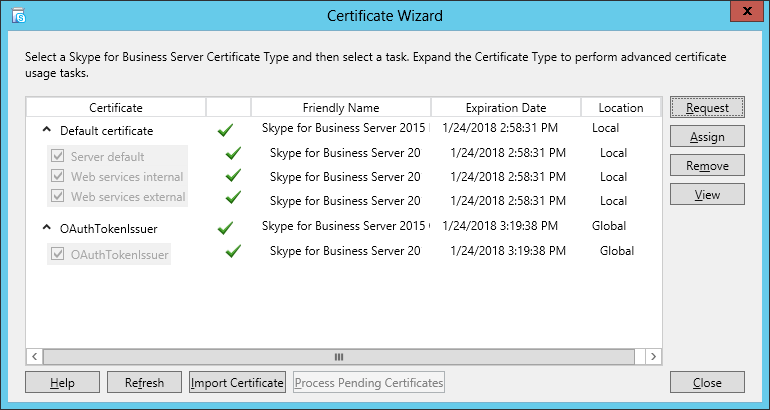
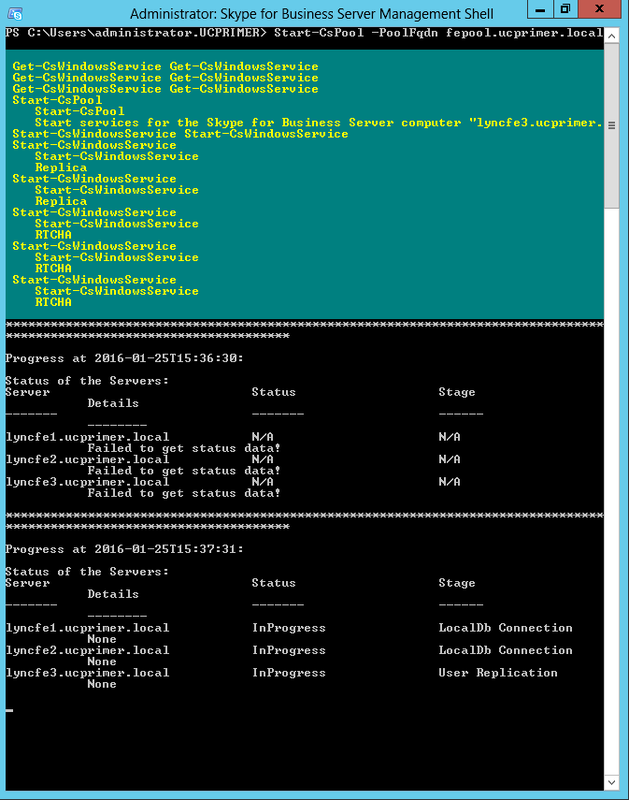
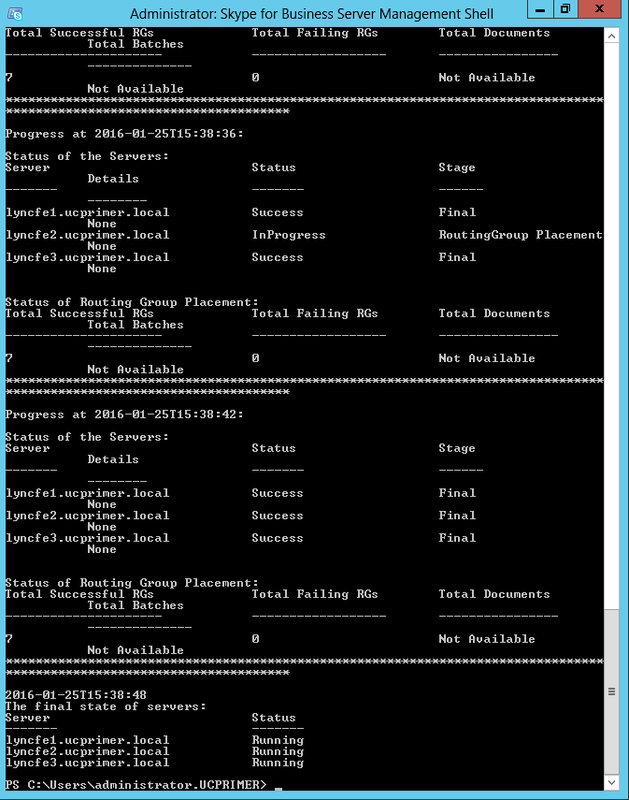
| Coming back to the office after a the year-end holidays like most people, I found that the Skype4B clients, IP Phones and Video Endpoints were no longer able to register with the Skype4B front-end pool. Yes time does pass very quickly and certificates that were created and assigned during installation do expire. The default expiry date for default FE server certificates is 2 years. This article explores the renewal of these FE certificates to get the system back to normal. |
| First and foremost, the client error message displayed during sign-in was rather misleading as this error was not due to DNS records at all. I suspect this could be due to the fact that this was a Hybrid setup with some users hosted on-premise and others hosted online on Office365. A quick check on the lyncdiscover.domain.com and lyncdiscoverinternal.domain.com DNS records as well as the fallback SRV records _siptinernaltls._tcp.domain.dom were correctly pointed to the on-premise FE Pool. Users who are homed online simply get redirected to the Office365 pool after they first hit the on-premise servers. Since the error cannot be due to DNS, then we need to look into the FE server itself to find out what the issue was. |



 RSS Feed
RSS Feed