| This article is intended for readers who are looking for guidance on how to deploy Lync 2013 Hybrid Split Domain with shared SIP address space. It documents the steps necessary to move from a fully on-premise Lync2013 deployment to a hybrid Office365 Lync split-domain deployment where some users are homed on-premise while some are homed on-line. Hopefully this serves as a useful reference to compliment the documentation already provided by TechNet. Do note that this is a very long article! |
federation enabled and all modalities working properly. All the necessary external and internal DNS records are already in-place and public SSL certificates are already assigned to the Lync Edge services and Reverse Proxy services. At the same time, an enterprise Office365 tenant to build the split domain topology on must also be available. In this setup an O365 E3 tenant is used for the hybrid deployment. Readers who do not have a tenant can sign up for a 30-day E3 trial here. Note also that the desired shared SIP address space must be a publicly verifiable domain therefore domain suffixes such as ".local" will not work. Ownership of the SIP domain is also required along with the ability to create public DNS records and purchasing of public SSL certificates. With all these in place, a quick overview of the steps involved is summarized below:
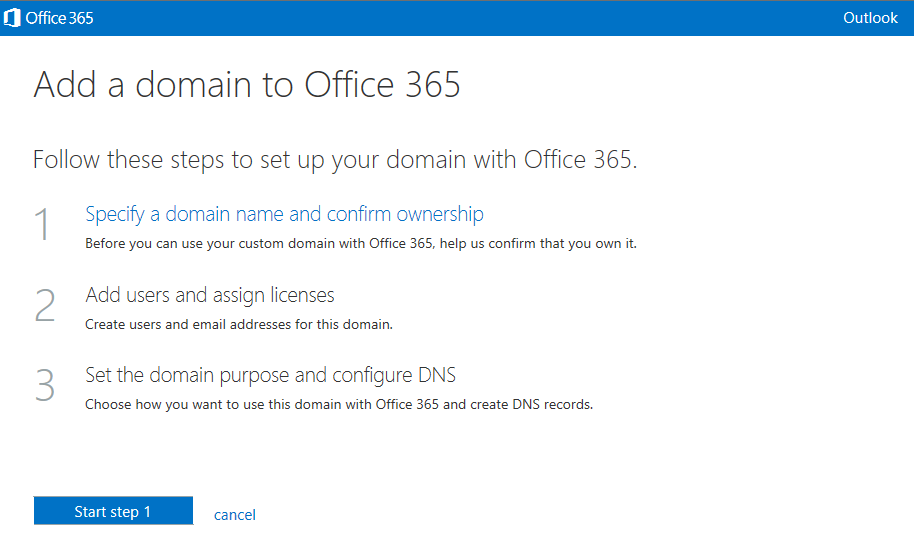
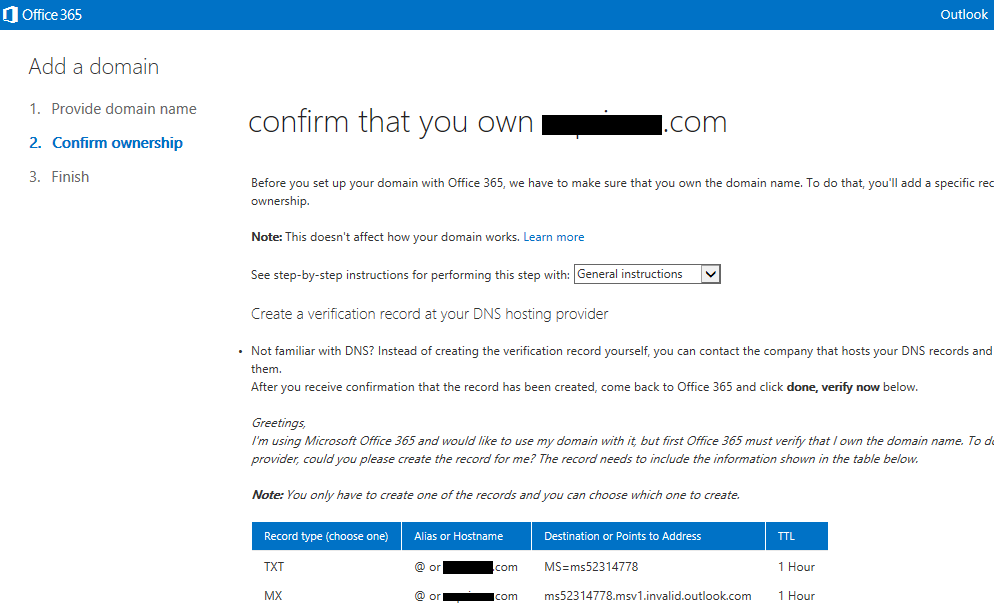
- Add your domain and verify ownership
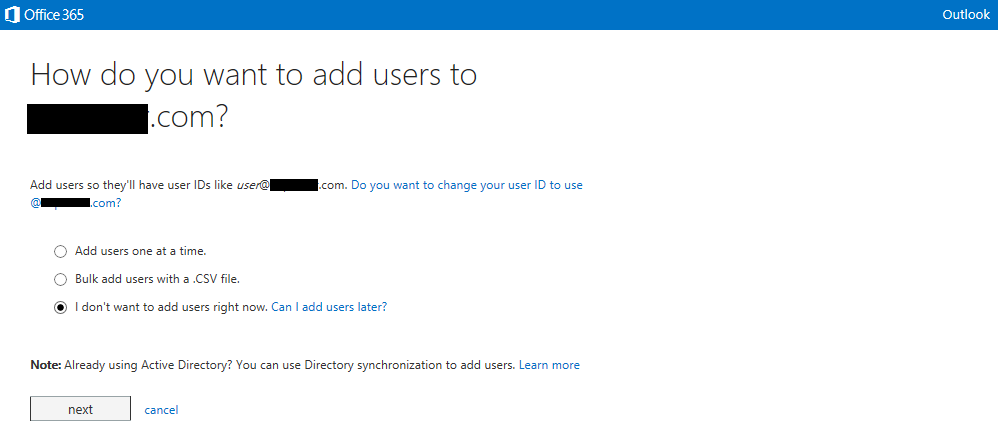
- Install and Configure Active Directory synchronization
- Install and Configure Active Directory Federation Services (AD FS)
- Install and Configure Active Directory Federation Services Proxy (AD FS Proxy)
- Configure Single Sign-on (SSO) with ADFS
- Configure federation of Lync Server 2013 with Lync Online
- Move user to Lync Online and test calls between Lync Online and Lync Onprem
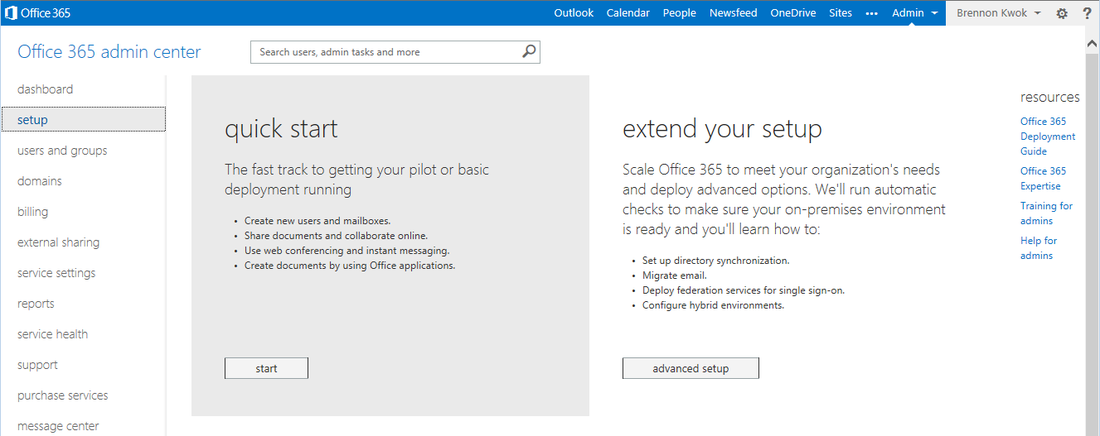
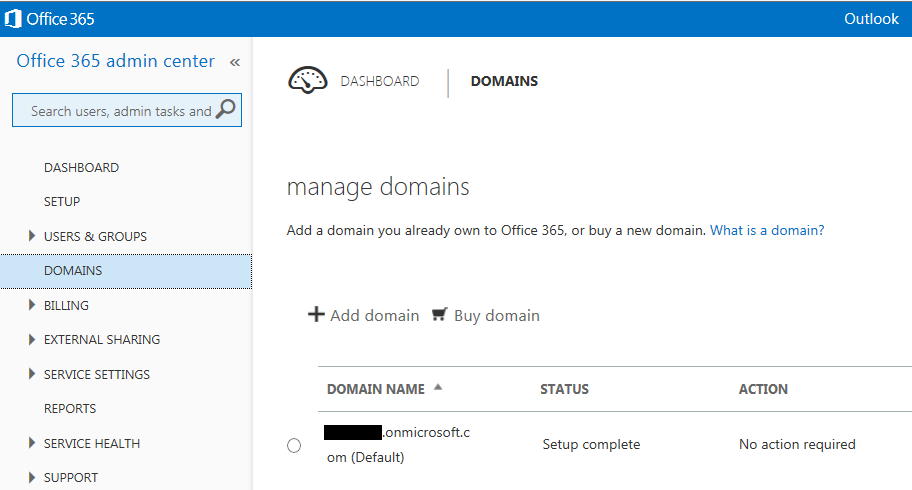
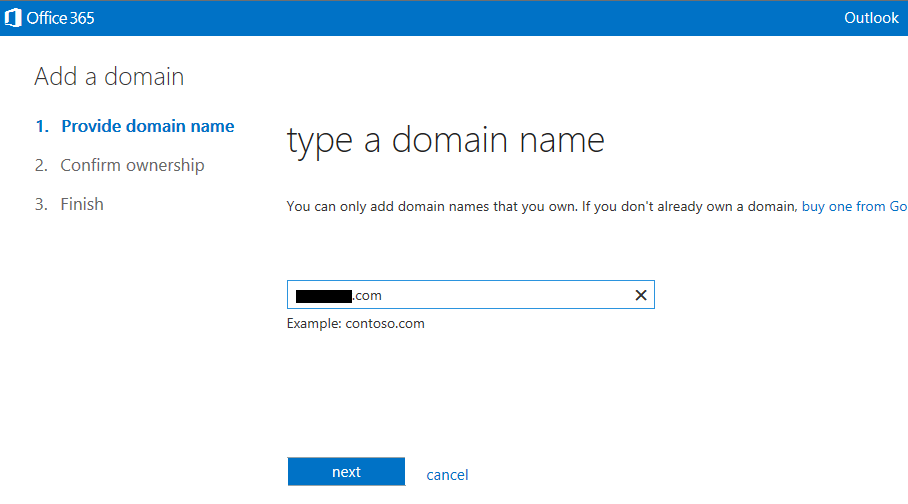
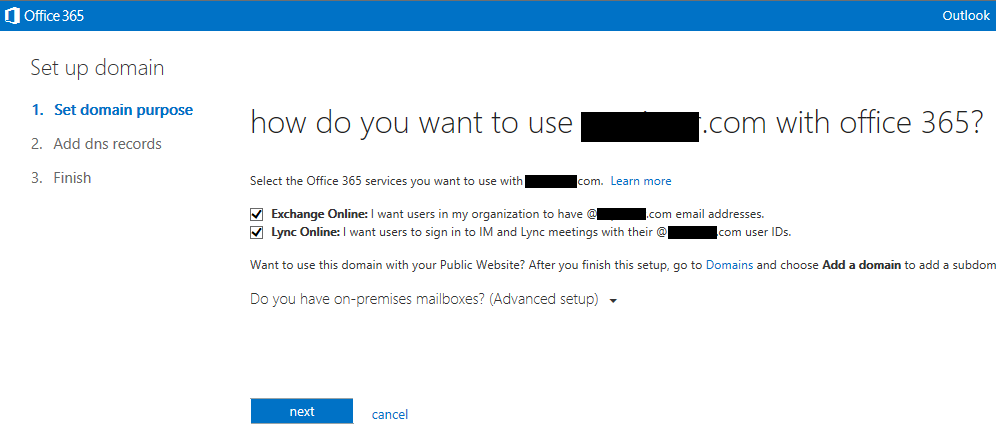
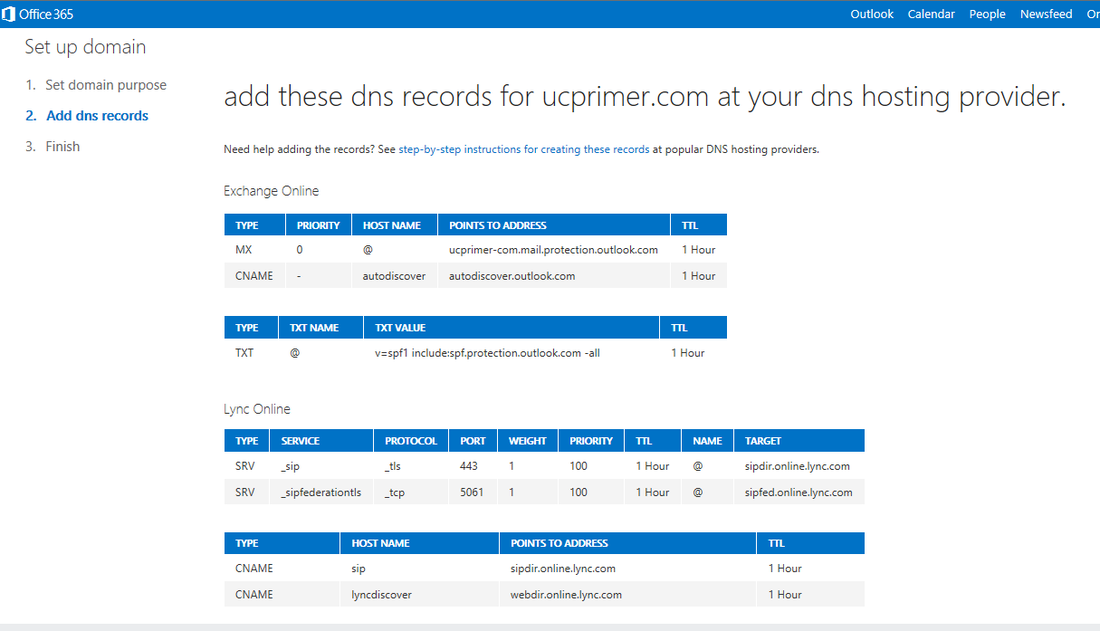
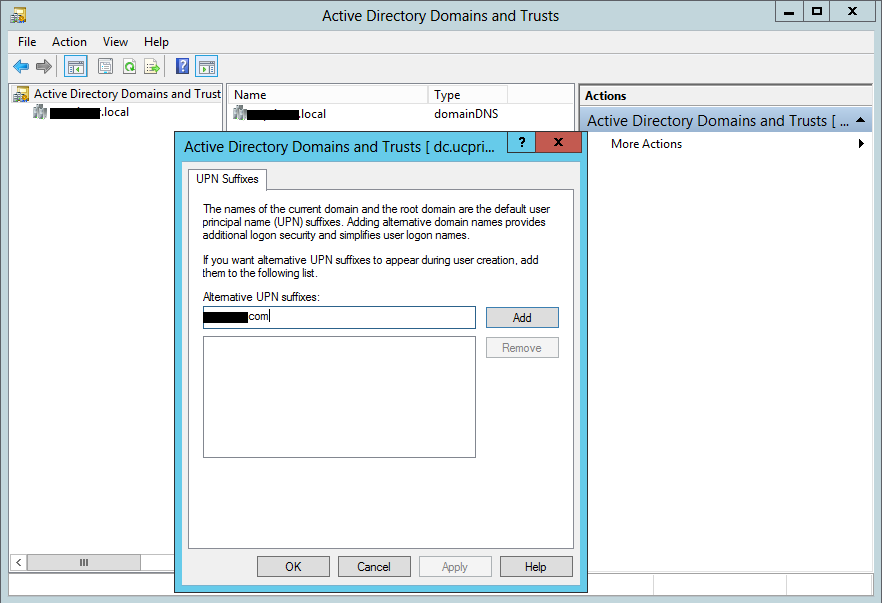
With an O365 E3 tenant account setup with the default options, the Online Lync SIP address and AD UPN suffix will be like mydomain.onmicrosoft.com. It is also good to test logins to this account using Lync and Exchange to make sure everything is working. The first tenant online user is typically also the administrator this account will be used for administration and setup of the hybrid environment. At this stage, there is no need to create any additional users on the tenant as user accounts will be synchronized from your Onprem AD later in step 2. The Onprem Lync SIP address and AD UPN desired will be something like mydomain.com, and this will be the shared SIP address space. We now need to add this "vanity" domain to the online tenant so that online users will also use the shared SIP address space. On the O365 admin center home page, click the "setup" tab and then "Start":
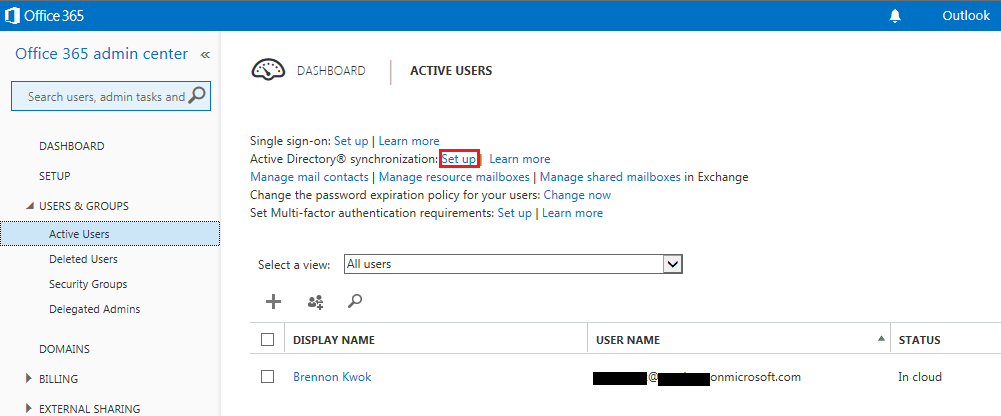
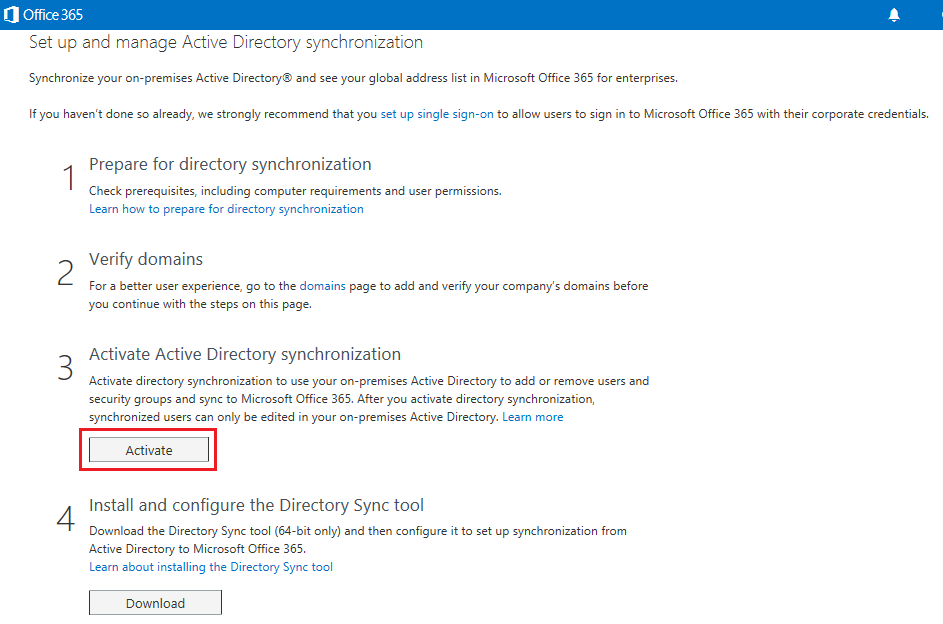
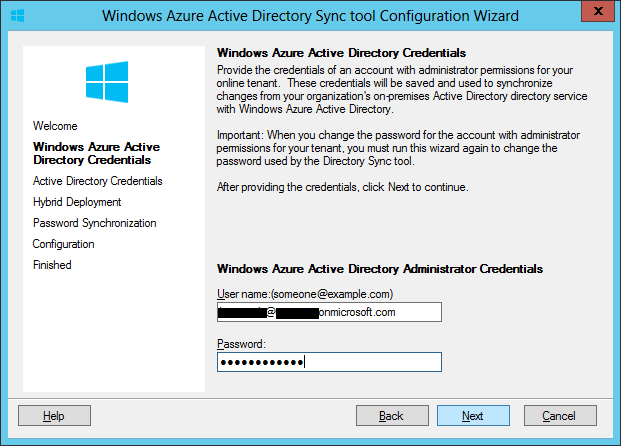
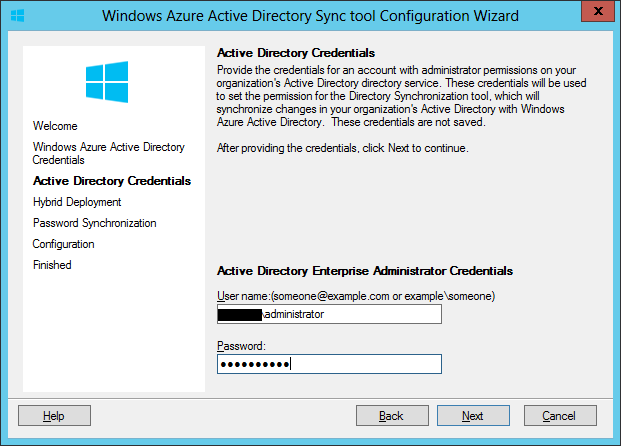
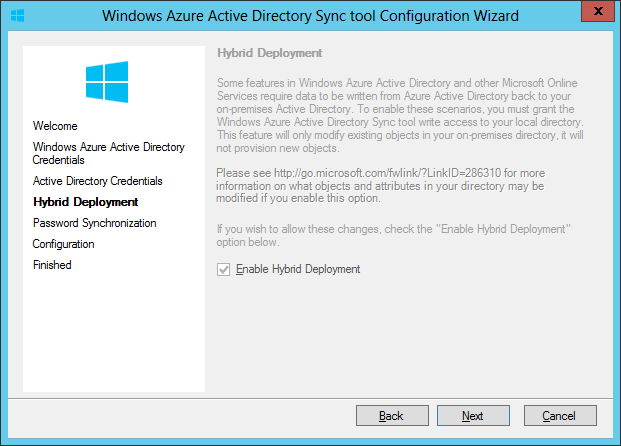
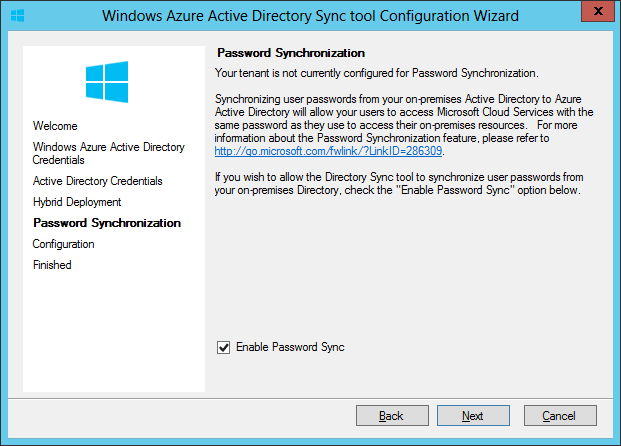
When setting up hybrid environment, Directory Synchronization or DirSync is mandatory, while there are two options for access control: Password Sync and Single Sign-on. For simplicity Password Sync can be used along with DirSync but this means that although user's password hash will be synchronized from On-prem AD to Azure AD, the user must login again to O365 in addition to the On-prem AD. SSO with DirSync requires a more complex setup involving ADFS and is shown later in this walk-thru. To begin, on the O365 admin center click on "Users & Groups" then click "Set up" for AD synchronization:
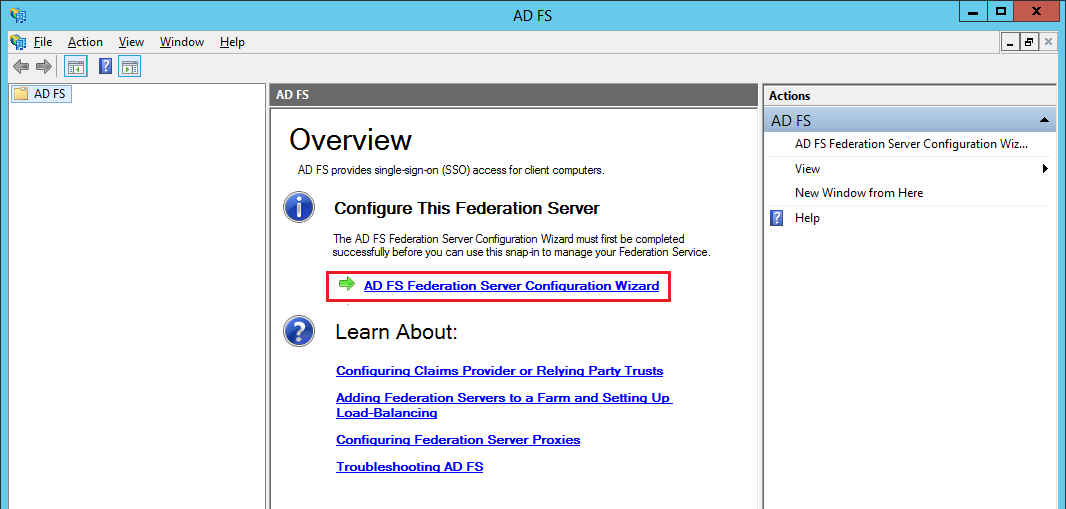
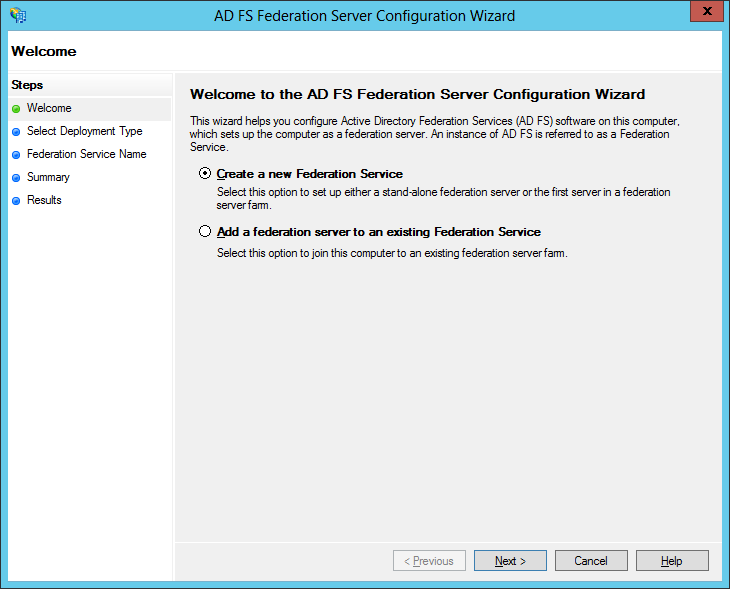
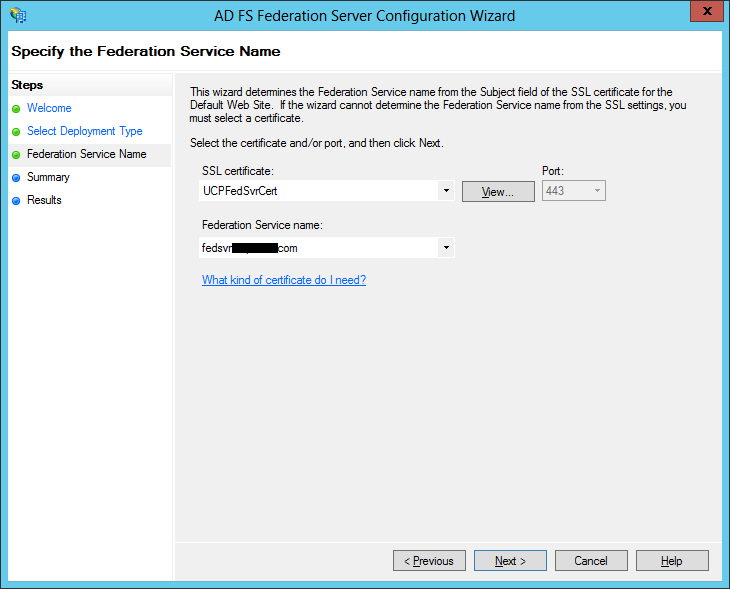
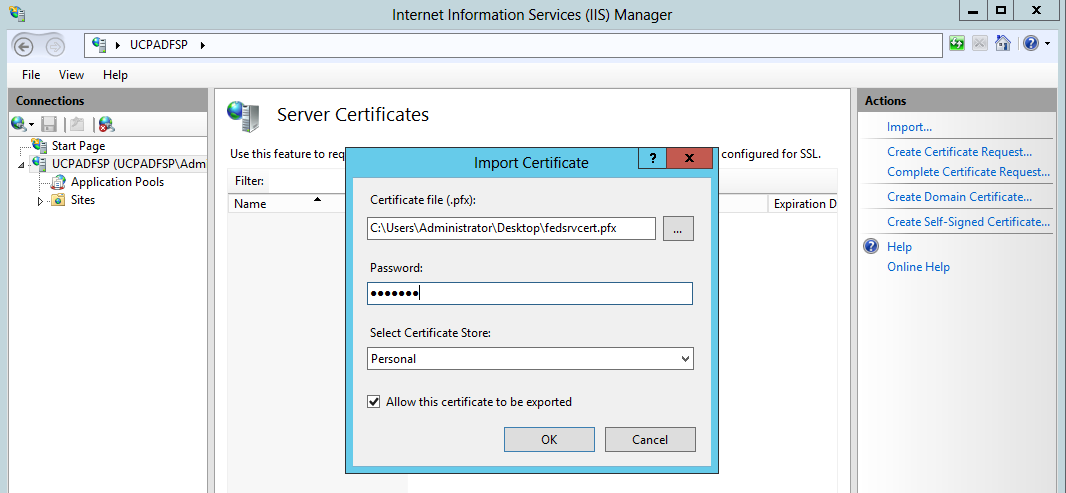
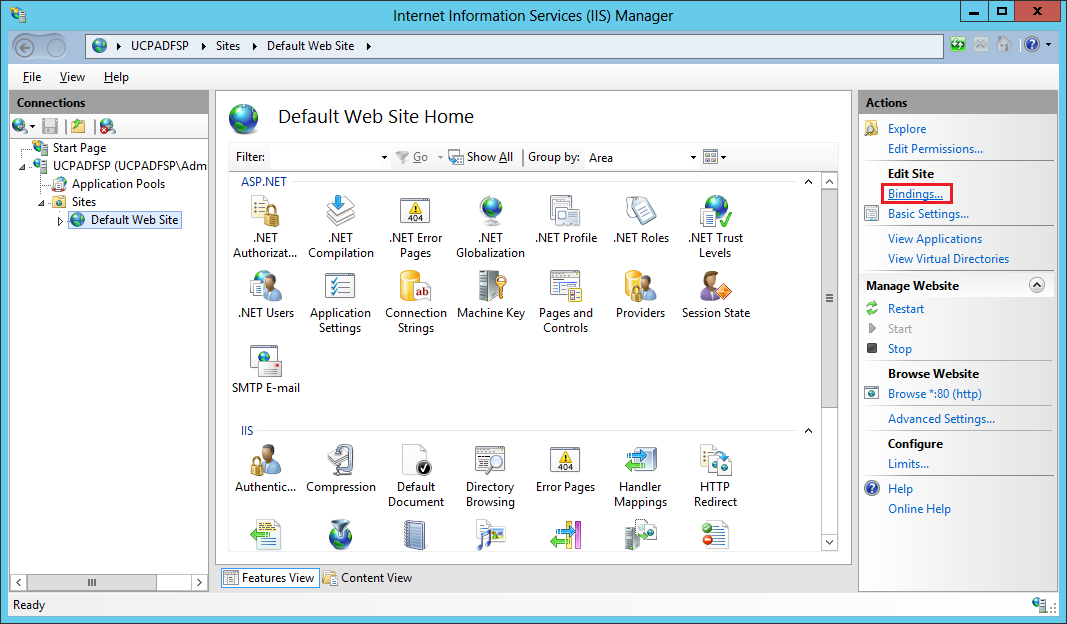
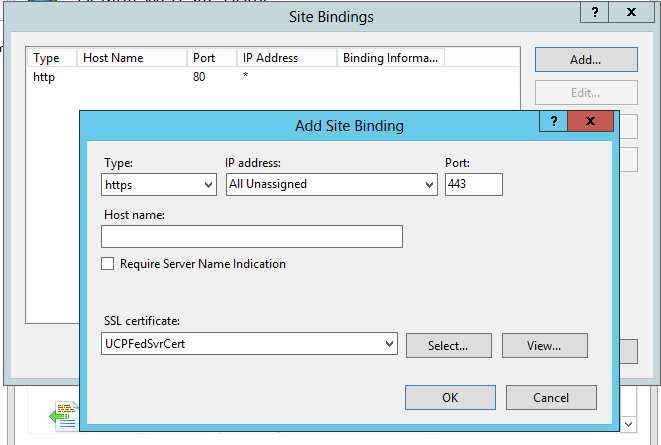
With DirSync configured, we next proceed to install and configure ADFS on Windows 2012. Note that you can install ADFS on a separate server but in this walk thru we will just use the same DC. Before beginning the installation, we will need to obtain a public SSL server authentication certificate. The Common Name or Subject Name of this certificate needs to match the name of the federated service, for this example we are using "fedsvr.mydomain.com". For this lab we created a certificate request using IIS on the DC and used this to purchase a standard, not UCC, SSL certificate from GoDaddy. After getting the certificate we imported it back into IIS (refer to this TechNet page for the steps to do this).
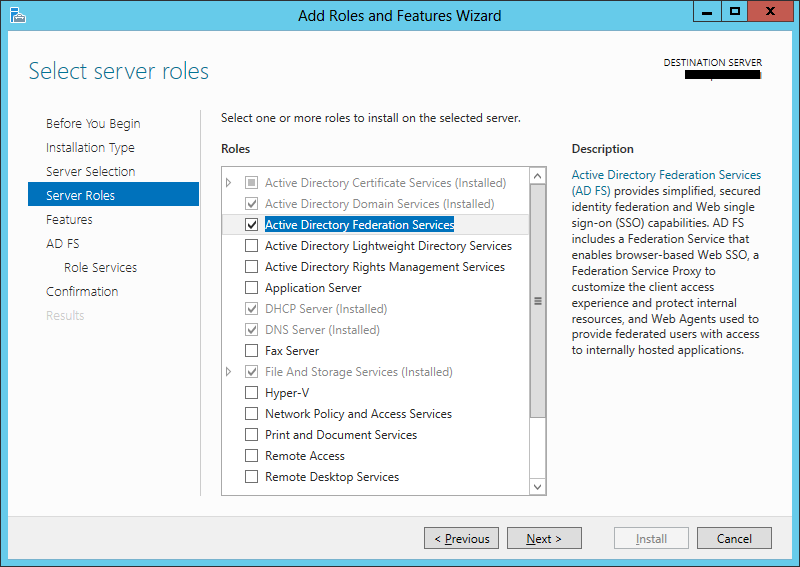
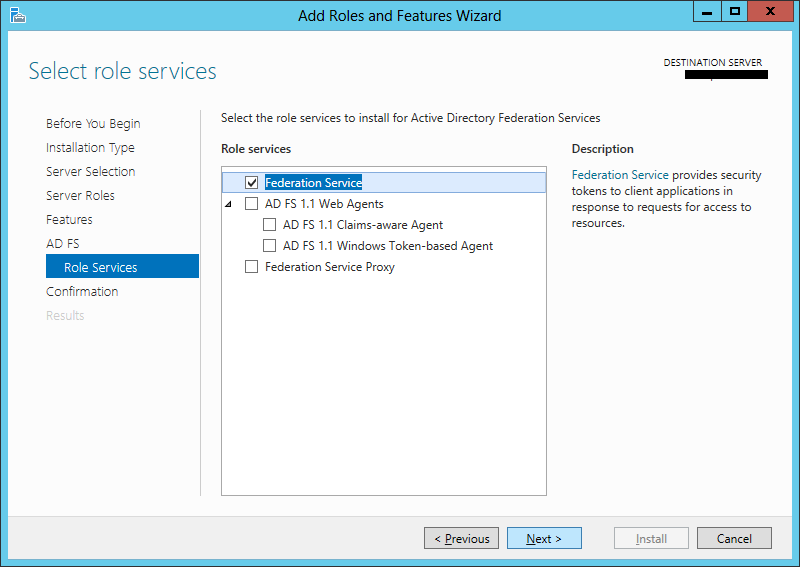
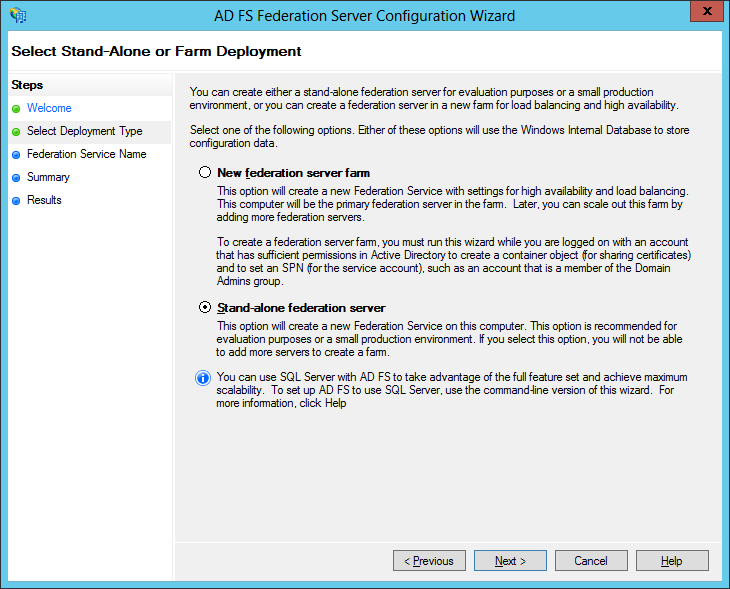
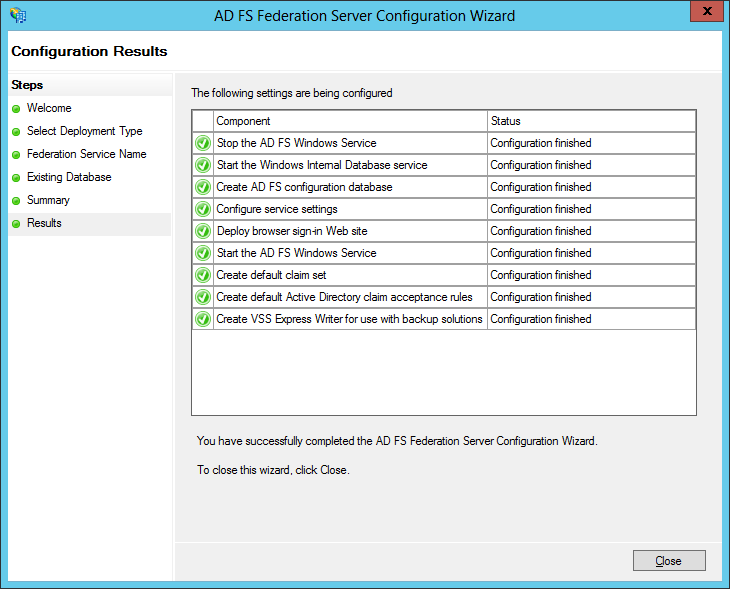
After that is complete, we can proceed to add the ADFS role to the DC:
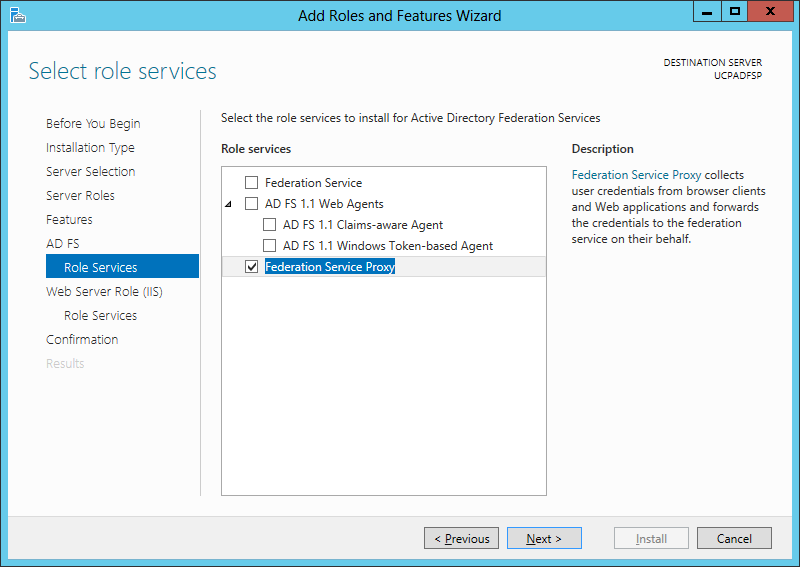
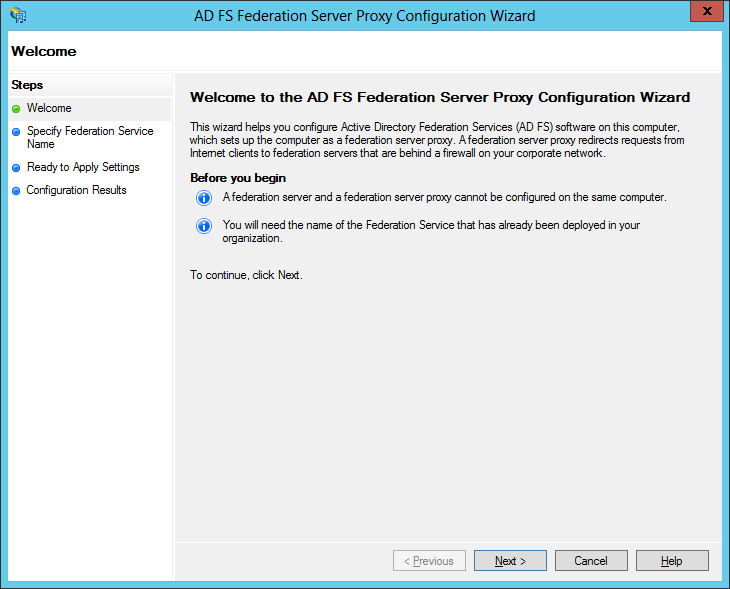
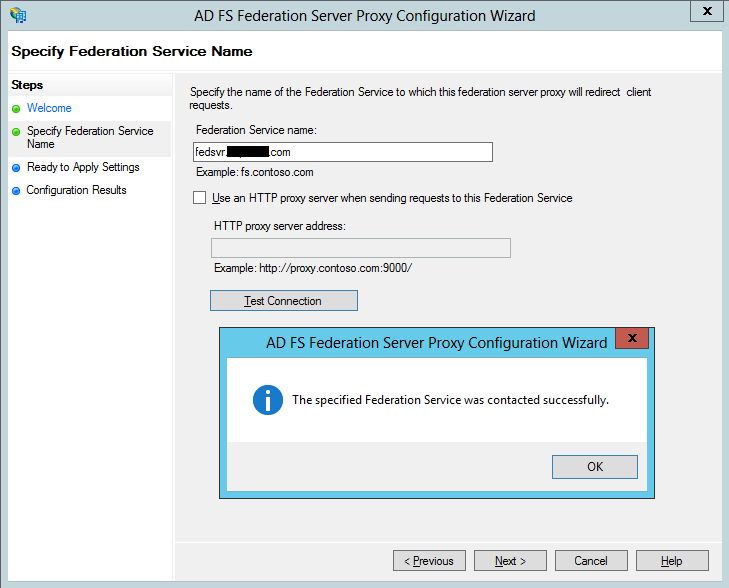
The ADFS proxy computer resides in the perimeter network and therefore cannot be collocated on the ADFS server. In this setup we installed a new Windows Server 2012 machine with 2 NIC cards for internal and external interfaces. The external interface has a NAT'ed public IP address which is assigned public DNS A Record that matches the FQDN of the ADFS service, which in this lab is fedsvr.ucprimer.com. Note that this computer is not joined to the domain. To begin, use the Roles and Features Wizard to add the Federation Service Proxy on the Windows 2012 computer:
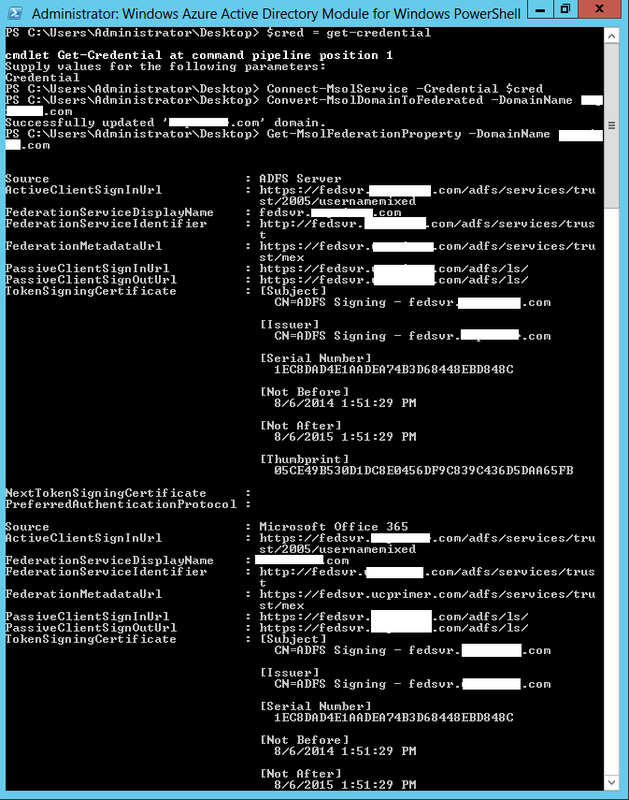
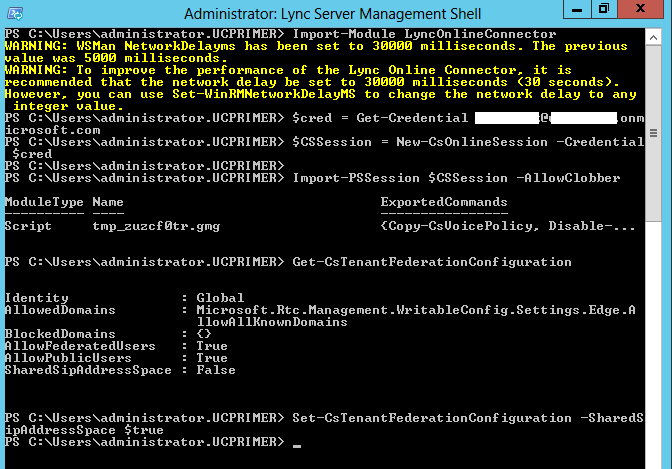
With the ADFS and ADFS Proxy setup, we can now configure SSO between the Onprem AD and O365's Azure AD. To begin, we download and install the Microsoft Azure Active Directory Module for Windows PowerShell on the ADFS computer. Once installed, open the module and run the following powershell commands to setup a trusted federation domain:
$cred = get-Credential // enter the tenant administrator credentials in the popup window
Connect-MsolService -Credential $cred
Convert-MsolDomainToFederated -DomainName <your AD domain>
Get-MsolFederationProperty -DomainName <your AD domain> // this is to verify successful setup
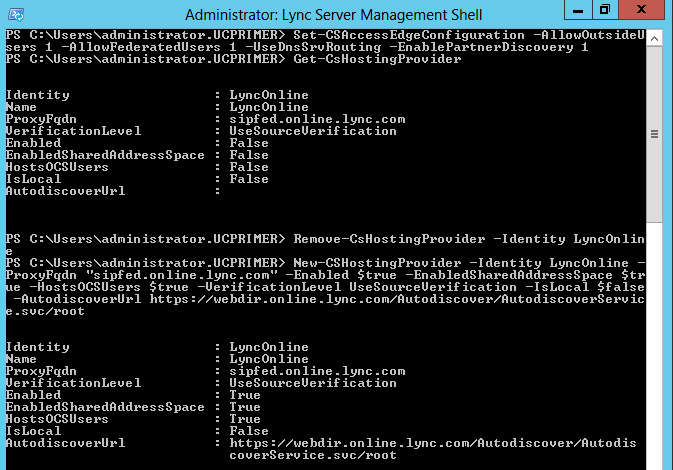
These series of powershell cmdlets are run from Lync Management shell to configure the necessary properties of the Onprem Lync for federation with Lync Online:
Set-CSAccessEdgeConfiguration -AllowOutsideUsers 1 -AllowFederatedUsers 1 -UseDnsSrvRouting
Remove-CsHostingProvider -Identity LyncOnline // Removes the default Lync Online Hosting Provider
New-CSHostingProvider -Identity LyncOnline -ProxyFqdn "sipfed.online.lync.com" -Enabled $true
-EnabledSharedAddressSpace $true -HostsOCSUsers $true -VerificationLevel UseSourceVerification -IsLocal
$false -AutodiscoverUrl https://webdir.online.lync.com/Autodiscover/AutodiscoverService.svc/root
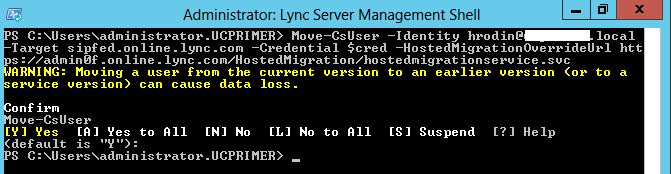
Move-CsUser : HostedMigration fault: Error=(510), Description=(This user’s tenant is not enabled for shared sip address space.)
To configure a shared SIP address space, establish a remote PowerShell session with Lync Online, and then run the following cmdlet:
Set-CsTenantFederationConfiguration -SharedSipAddressSpace $true
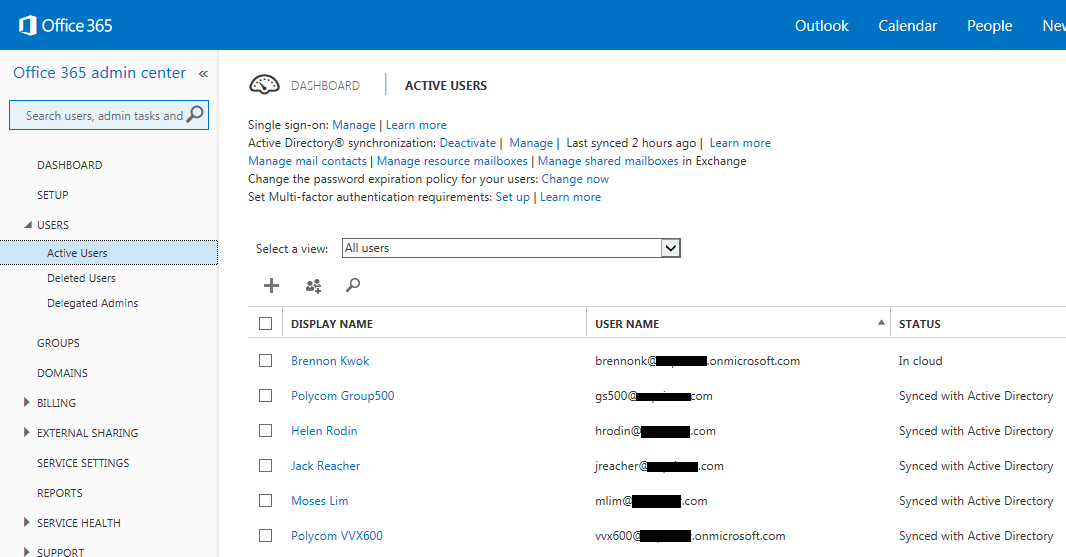
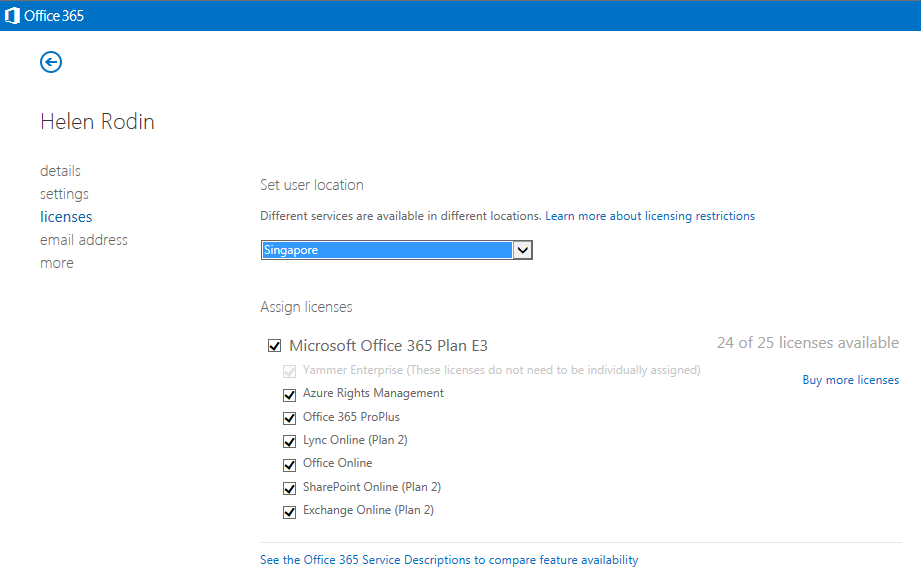
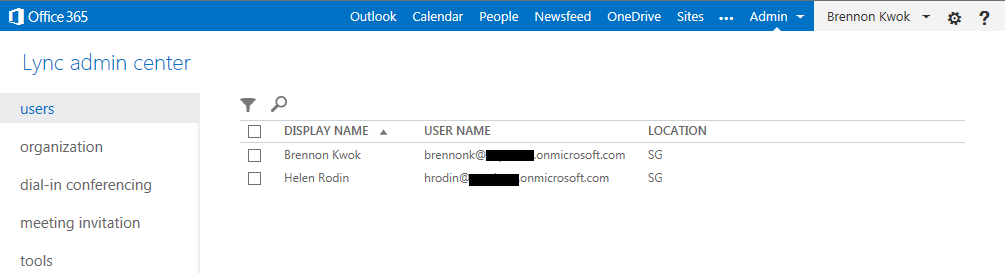
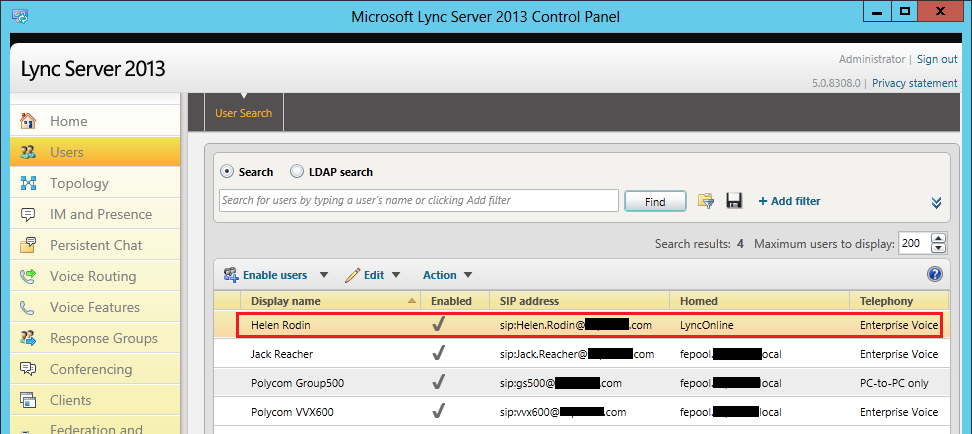
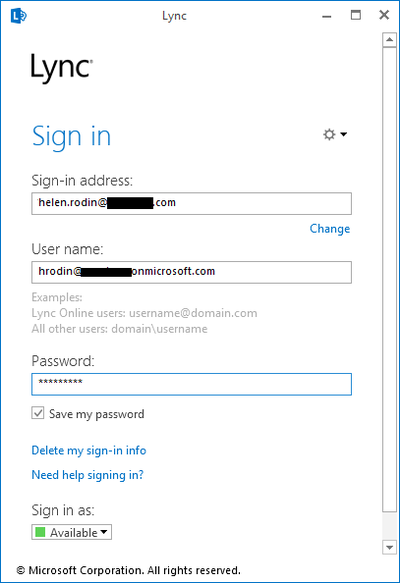
In the final stage, we move an existing Lync Onprem user to Lync Online. In this walk thru we move the user with SIP address [email protected] and AD UPN [email protected]. This user has already been enabled for Lync Onprem and is able to login from a Lync client. To begin the move process, we first login to the O365 admin page and assign a E3 license for this user:
Move-CsUser -Identity <user's AD UPN> -Target sipfed.online.lync.com -Credential $cred -HostedMigrationOverrideUrl <Hosted migration override URL for your tenant>


 RSS Feed
RSS Feed